Protecting Your Digital Haven: The Vital Role of Hard Drive Encryption
In our increasingly interconnected world, the safety of our digital data is paramount. Every file, photo, and piece of personal information stored on our devices represents a part of our lives, and the thought of it falling into the wrong hands is unsettling, to say the least. This is where hard drive encryption steps in as a crucial line of defense—a virtual fortress protecting our most sensitive information from prying eyes and potential threats.
Think of your hard drive as a digital vault, safeguarding your valuable data from the outside world. Now, imagine that vault without a lock—an open invitation to anyone who stumbles upon it. Hard drive encryption acts as that lock, securing your data behind an impenetrable barrier unless you possess the key. By scrambling the contents of your hard drive into an unreadable format, encryption ensures that even if your device falls into the wrong hands, your data remains safe and inaccessible without the proper authorization.
Below I will demonstrate step by step a technical threat actor compromise on a machine disabling its securities and infecting the system with malware.
Initial Compromise Scenario
I went ahead and created a virtualized environment to demonstrate a POC of how a full machine compromise can happen to anyone if they leave their machine unattended with physical access. We'll focus on the scenario where a threat actor finds an unattended machine with "Bob's" account logged in.
The threat actor doesn't know Bob's password but remembers a modern Windows flaw that allows manual password changes for local accounts with ease due to no encryption on the drive. Step one is to restart WHILE HOLDING shift.
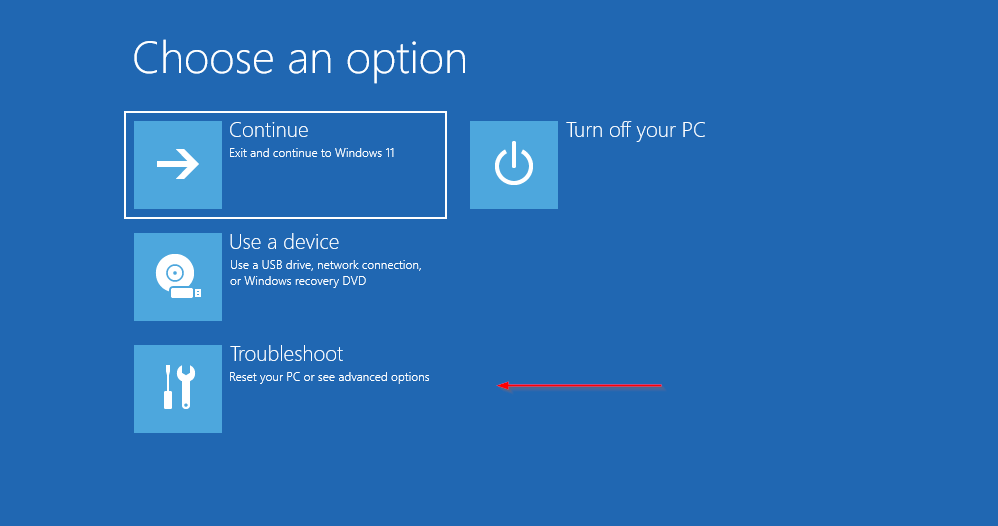
Accessing Advanced Options
After the computer reboots, click troubleshoot, then click advanced options.
Command Prompt Access
Select command prompt from the options.
System32 Manipulation
Navigate to the system32 folder on the primary drive (C: drive). By typing the commands shown in the images, we're renaming the utility tool in Windows sign-in called utilman.exe and replacing it with cmd.exe.
This allows the threat actor to access Bob's login page by clicking utility assistance, which will now open a command prompt instead.
Password Reset
After clicking the utility button, we can see cmd popped up and can be used to reset Bob's local account password.
System Penetration
Just like that, Bob's password was changed and the threat actor gains access. Next, they check what defenses the endpoint has and see it's on the latest Windows update.
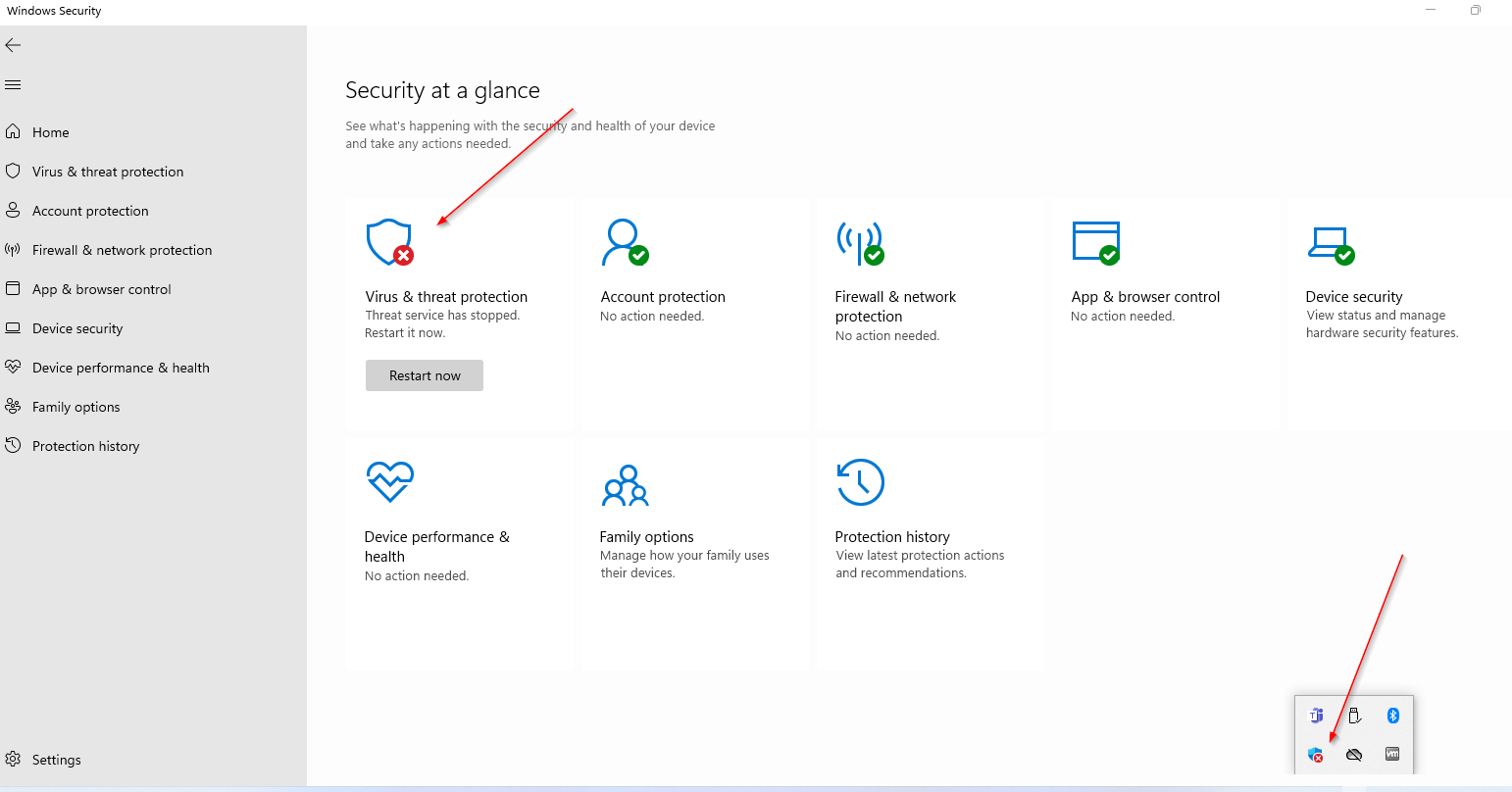
Defender Disabling
Most advanced threat actors have methods to either bypass defender or remove it entirely. This method aims to remove defender from the system for permanent persistence using a custom script that disables defender from the root.
PowerShell Execution
I grabbed my custom PowerShell script named 1.ps1. For this to work, we need to boot the system in safe mode since the password was already changed. Then we execute the PowerShell command disabling Windows Defender.
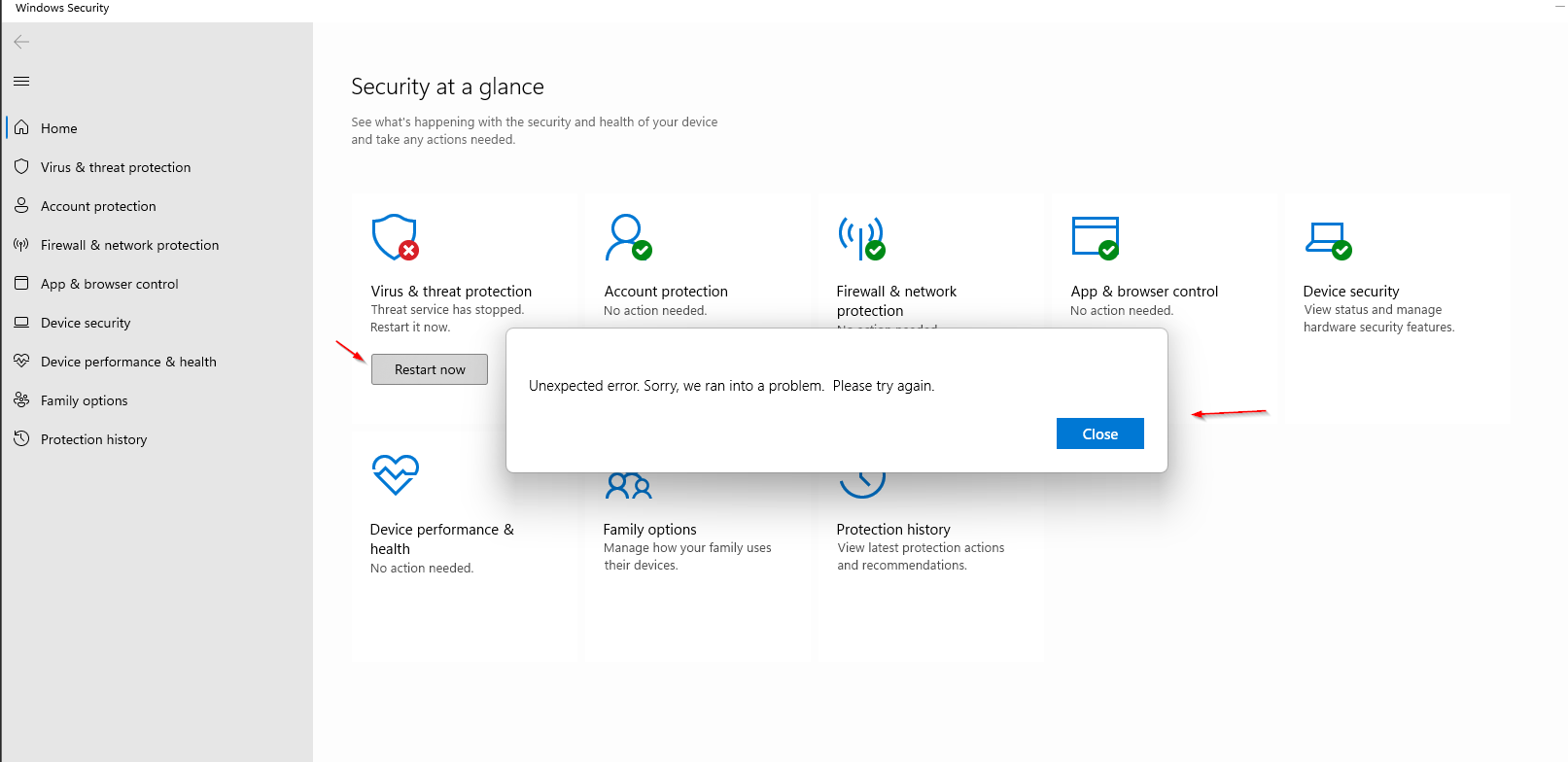
Malware Deployment
After rebooting and seeing that virus protection shows as unknown, I deployed a malicious binary hosted by Pentagon RAT while defender notifications are still showing as off.
Full System Compromise
And BOOM - a connection was made to Bob's computer and it's now fully pwned by the C2 Pentagon RAT. The RAT shows its full capabilities on the right-hand side and no AV or EDR is there to stop it, providing excellent persistence.
NOTE: This method can be used with any malicious software - this is just an example.
Project Jericho - Stealth Enhancement
For better stealth, I created Project Jericho - a tool that grabs all Microsoft Security related registry keys including real-time monitoring, UAC, Exploit Guard, LSA protection, etc., and inverses the keys to remove registry artifacts and brick defender's security.
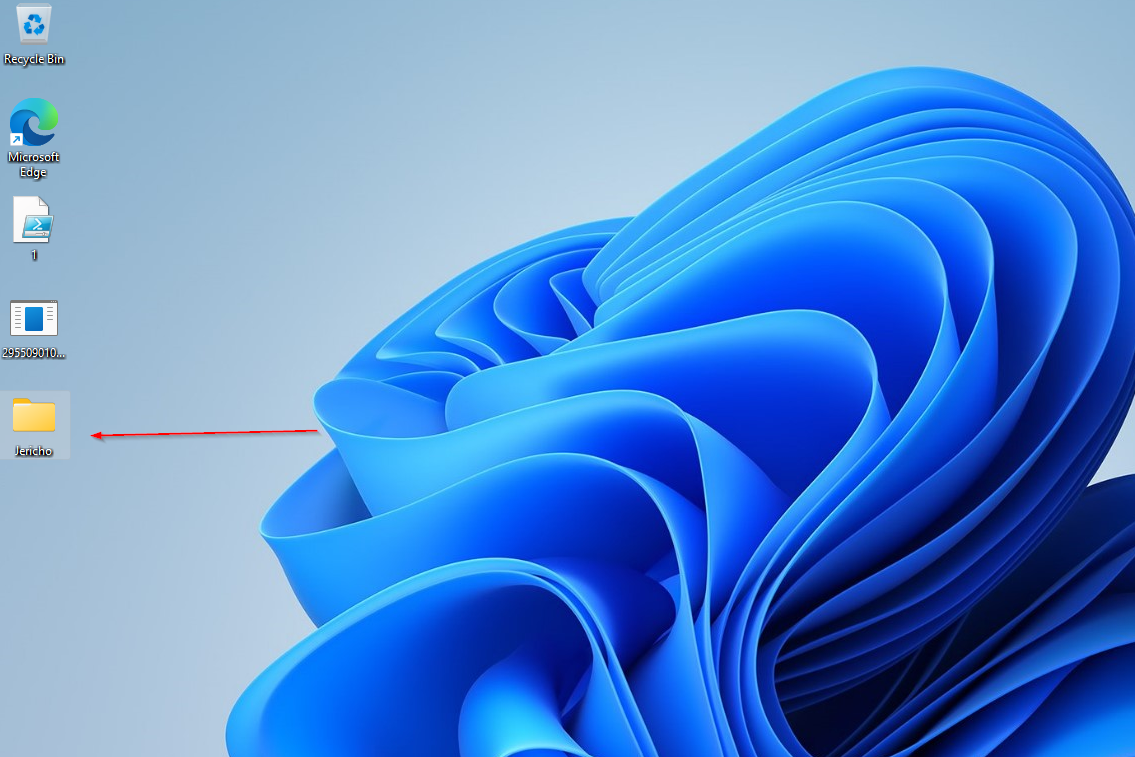
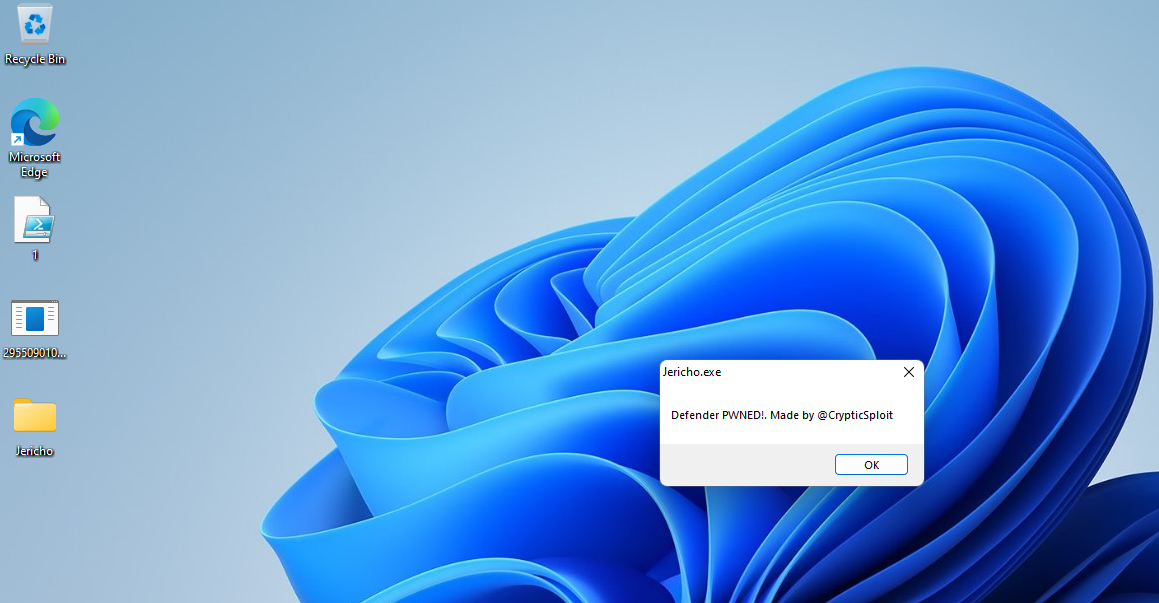
Complete Security Removal
After running Jericho, I got notification that the system was pwned and remaining defender artifacts were removed. The Windows Defender icon disappeared completely, meaning no more status notifications to warn users.
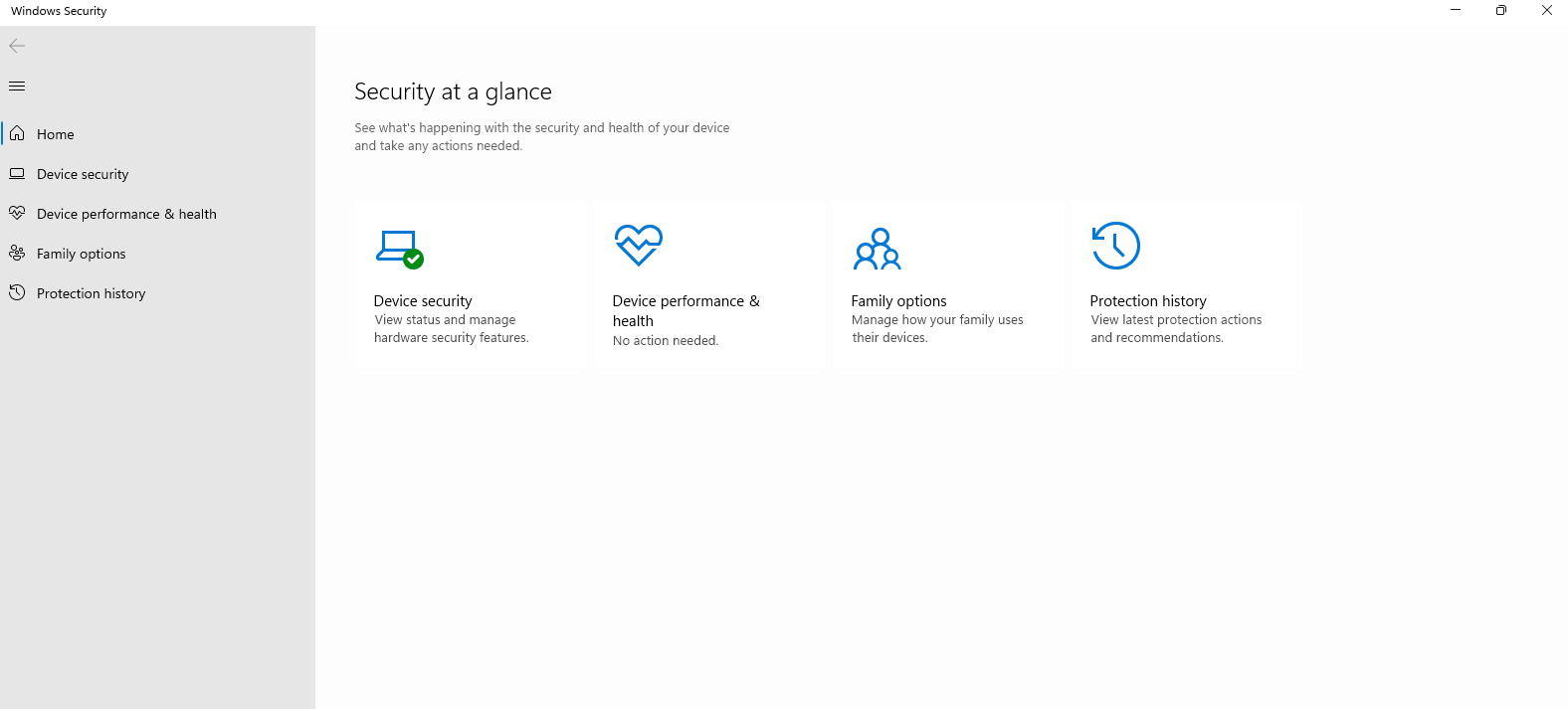
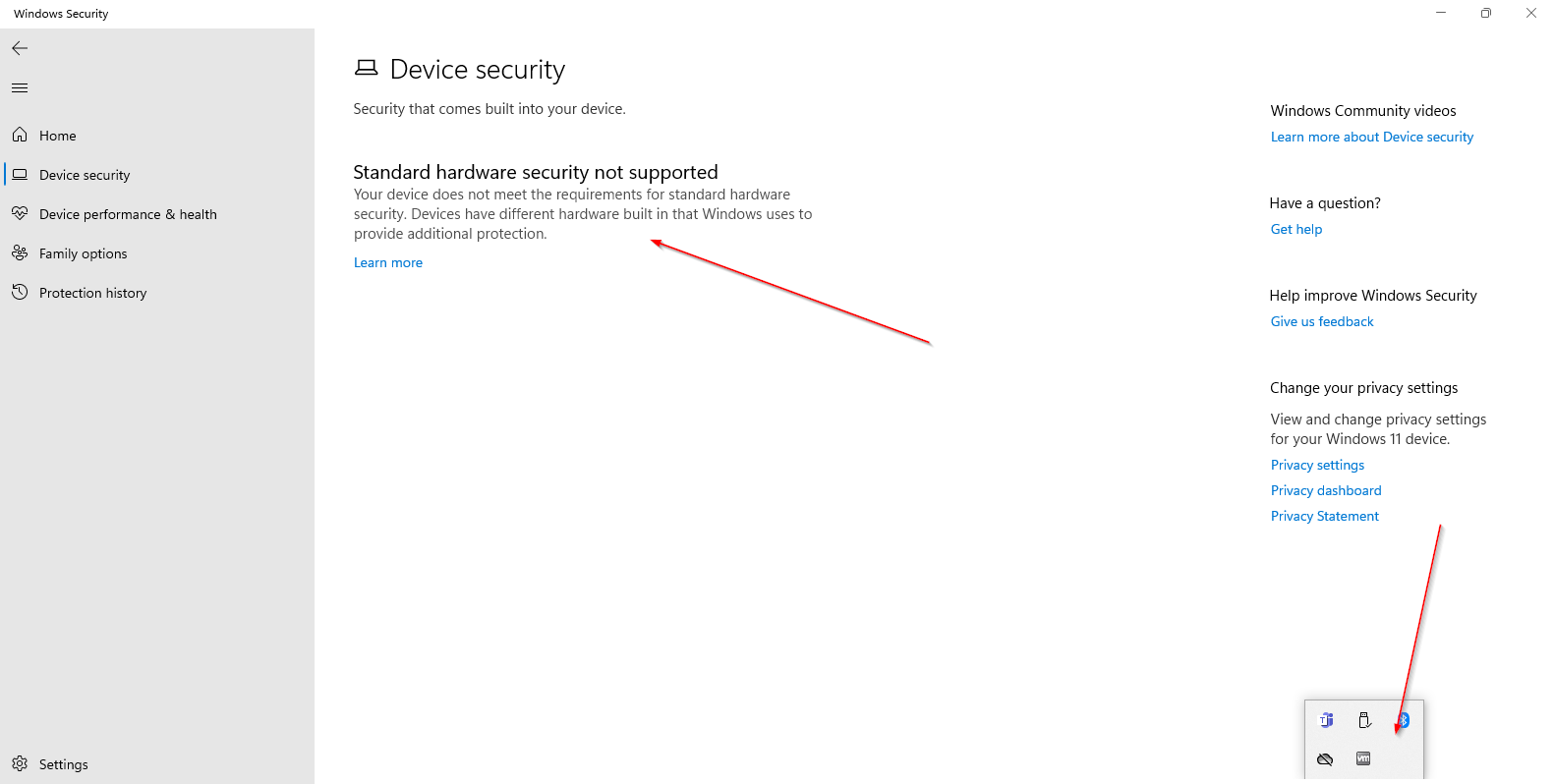
Persistent Access Confirmed
After fully removing Defender and rebooting, the Windows Security UI changed completely. The backdoor connection to the C2 RAT panel remained active, confirming successful persistent access to the compromised system.
Key Takeaways
This demonstration shows how critical hard drive encryption is for protecting your data. Without encryption, a threat actor with physical access can completely compromise your system, disable security measures, and establish persistent backdoors. The importance of implementing full disk encryption cannot be overstated in today's threat landscape.
